An unknown attacker is actively exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress.
This vulnerability is described as a case of broken access control and affects versions 3.11.6 and earlier. This issue was addressed by the plugin maintainers in version 3.11.7, released on March 22nd.
“Enhancing code security for WooCommerce components”, a Tel Aviv-based company Said to the release notes.premium plugins Estimate Used by over 12 million sites.
Successful exploitation of a high-severity flaw allows an authenticated attacker to complete a takeover of a WooCommerce-enabled WordPress site.
“This would allow a malicious user to enable the registration page (if it was disabled) and set the default user role to administrator, instantly creating an account with administrator privileges. .” Said On March 30, 2023 alert.
“After this, they may redirect the site to another malicious domain or upload malicious plugins or backdoors to further abuse the site.”
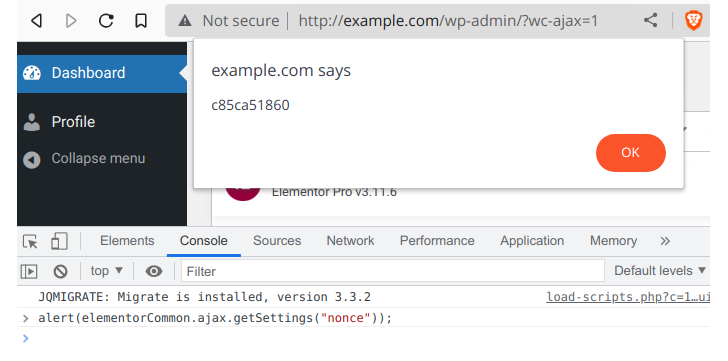
credit Vulnerability discovery and reporting Date 18 March 2023 is Jerome Bruandet, NinTechNet security researcher.
Patchstack also noted that this vulnerability is currently being exploited from multiple IP addresses attempting to upload arbitrary PHP and ZIP archive files.
Elementor Pro plugin users are advised to update to the latest version 3.11.7 or 3.12.0 as soon as possible to mitigate potential threats.
Become an Incident Response Pro!
Unlocking the Secrets of Bulletproof Incident Response – Master the 6-step process with Asaf Perlman, IR Lead at Cynet!
This advisory comes more than a year after it was discovered that the Elementor plugin Essential Addons contained a critical vulnerability that could allow arbitrary code execution on compromised websites. increase.
Last week, WordPress issued an automatic update to fix another critical bug in its WooCommerce Payments plugin that allowed unauthenticated attackers to gain admin access to vulnerable sites.


