Microsoft shared guidance on Friday to help find indicators of compromise (IOCs) related to the recently patched Outlook vulnerability.
being tracked as CVE-2023-23397 (CVSS score: 9.8), serious flaw Related to privilege escalation cases where NT Lan Manager (NTLM) hashes can be stolen and exploited to perform relay attacks without requiring user interaction.
“An outside attacker could send a specially crafted email that causes a connection from the victim to an untrusted location under the attacker’s control,” the company said. I got it In an advisory released this month.
“This leaks net NTLMv2 hash Victim to an untrusted network where the attacker can relay to another service and authenticate as the victim.
Although this vulnerability was resolved by Microsoft as part of the March 2023 Patch Tuesday update, Russia-based attackers targeted European government, transportation, energy, and military sectors. It wasn’t before weaponizing the attack flaws to attack.
Microsoft’s incident response team says it has found evidence that this vulnerability could be exploited as early as April 2022.
In one attack chain described by the tech giant, a successful Net-NTLMv2 relay attack allowed the attacker to gain unauthorized access to an Exchange Server and modify mailbox folder permissions for permanent access. is ready.
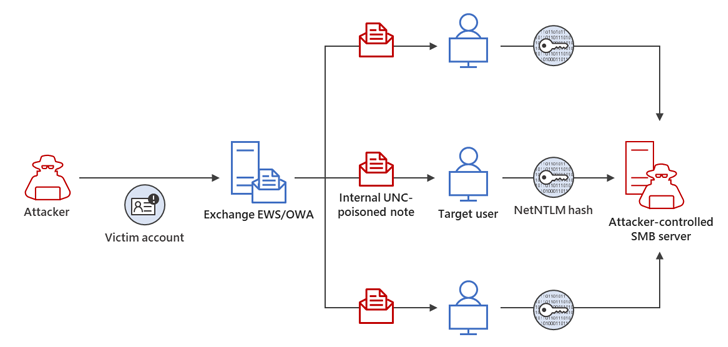
The compromised email account was used to extend the attacker’s access within the compromised environment by sending additional malicious messages targeting other members of the same organization.
“Although leveraging NTLMv2 hashes to gain unauthorized access to resources is not a new technique, the exploitation of CVE-2023-23397 is novel and stealthy,” Microsoft said. Said.
“Organizations should review SMBClient event logs, process creation events, and other available network telemetry to identify potential exploits for CVE-2023-23397.”
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
This disclosure is made as the United States Cybersecurity and Infrastructure Security Agency (CISA). release A new open source incident response tool that helps detect signs of malicious activity in Microsoft cloud environments.
dubbing untitled goose toola Python-based utility that provides “new authentication and data collection methods” for analyzing Microsoft Azure, Azure Active Directory, and Microsoft 365 environments.
Earlier this year, Microsoft urged customers to take steps to keep their on-premises Exchange servers up to date and harden their networks to mitigate potential threats.


