Banks and financial services organizations have been targeted in new multi-stage man-in-the-middle (AitM) phishing and business email compromise (BEC) attacks, Microsoft has revealed.
“The attack originated from a trusted vendor that was compromised and moved into a series of AiTM attacks and subsequent BEC activity across multiple organizations,” said the technology giant. disclosed in Thursday’s report.
Microsoft tracking cluster under new name Arashi-1167claimed the group used an indirect proxy to carry out the attack.
This gives attackers the flexibility to tailor phishing pages to their targets and perform session cookie theft, highlighting the continued sophistication of AitM attacks.
This technique differs from other AitM campaigns where the decoy page acts as a reverse proxy to collect victim-entered credentials and time-based one-time passwords (TOTPs).
“The attacker presented the target with a website that mimicked the target application’s sign-in page, similar to traditional phishing attacks hosted on cloud services,” Microsoft said.
“The above sign-in page contained resources loaded from an attacker-controlled server and used the victim’s credentials to initiate an authentication session with the target application’s authentication provider.”
The attack chain starts with a phishing email pointing to a link. Upon clicking the link, the victim is redirected to her fake Microsoft sign-in page to enter her credentials and her TOTP.
Collected passwords and session cookies are used to impersonate users and gain unauthorized access to email inboxes through replay attacks. This access is then exploited to retrieve sensitive emails and plan BEC attacks.
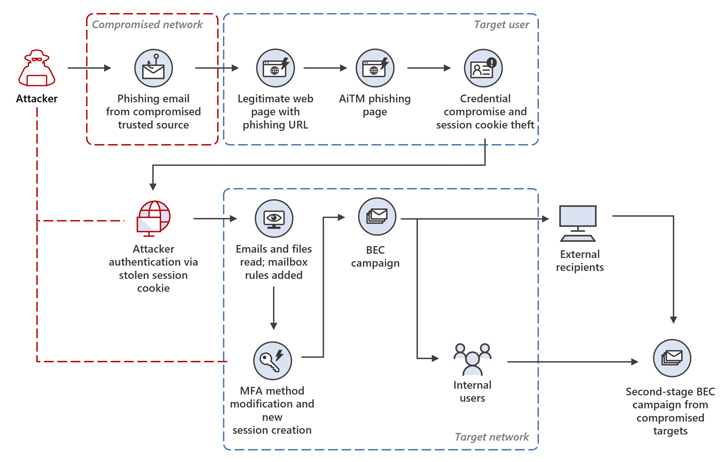
Additionally, a new SMS-based two-factor authentication method is added to the target account so that you can sign in using stolen credentials without attracting attention.
In this incident analyzed by Microsoft, the attackers allegedly launched a mass spam campaign, sending more than 16,000 emails to contacts and distribution lists inside and outside the organization of compromised users.
Attackers have also been observed taking steps to minimize detection and establish persistence by responding to incoming emails and then deleting them from mailboxes.
Ultimately, the recipient of the phishing email was targeted in a second AitM attack, where credentials were stolen and yet another phishing campaign was triggered from the email inbox of one of the users whose account was hacked as a result of the AitM attack. will be
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join us for an insightful webinar!
“This attack demonstrates the complexity of the AiTM and BEC threats that exploit trust relationships between vendors, suppliers and other partner organizations for financial fraud,” the company added.
This development came less than a month from Microsoft. warned Learn about the surge in BEC attacks and the evolution of tactics employed by cybercriminals, including the use of platforms like BulletProftLink to craft industrial-scale malicious email campaigns.
Another tactic involves using residential Internet Protocol (IP) addresses to make the attack campaign look like it originated locally, the tech giant said.
“BEC threat actors then buy IP addresses from residential IP services that match the victim’s location and create residential IP proxies that allow cybercriminals to hide their origin,” said Redmond. explained.
“In addition to usernames and passwords, a BEC attacker with a localized address space to support their malicious activity can hide their movements, circumvent ‘immovable’ flags, and provide additional security to carry out further attacks. You can open the gateway.”



