Microsoft’s monthly patch update for March 2023 is rolling out with a series of fixes. 80 security flawstwo of which are actively exploited in the wild.
Of the 80 bugs, 8 were rated critical, 71 were rated critical, and 1 was rated moderate severity.the update is 29 flaws plus The Chromium-based Edge browser has been fixed in the last few weeks.
Two vulnerabilities under active attack include a privilege escalation flaw in Microsoft Outlook (CVE-2023-23397CVSS score: 9.8) and Windows SmartScreen security feature bypass (CVE-2023-24880CVSS score: 5.1).
CVE-2023-23397 “triggers when an attacker sends a message with extended MAPI properties with a UNC path to an SMB (TCP 445) share on a server controlled by the threat actor”, Microsoft Said In a standalone advisory.
By sending a specially crafted email, an attacker could exploit this vulnerability to automatically activate the email once retrieved and processed by the Outlook client for Windows. . As a result, it can be exploited without any user interaction required and before the message is displayed in the preview pane.
Microsoft confirmed that the Ukraine Computer Emergency Response Team (CERT-UA) had reported the flaw and said that the Russian-based threat actor had launched a “limited It added that it was aware of “targeted attacks”.
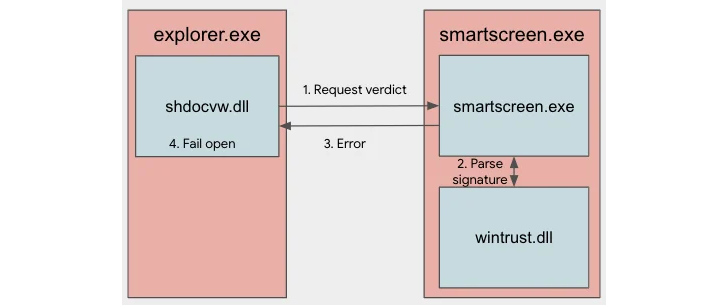
CVE-2023-24880, on the other hand, concerns a security bypass flaw that can be exploited to circumvent Mark-of-the-Web (MotW) protections when opening untrusted files downloaded from the Internet. is.
This is also the result of a narrow patch released by Microsoft to resolve another SmartScreen bypass bug (CVE-2022-44698, CVSS score: 5.4) that surfaced last year.
“Vendors often release narrow patches, creating opportunities for attackers to iterate and discover new variants,” said Benoit Sevens, a researcher at the Google Threat Analysis Group (TAG). increase. Said in the report.
“Because the root cause behind the SmartScreen security bypass was not resolved, the attackers were able to quickly identify another variant of the original bug.”
TAG said it has seen more than 100,000 downloads of malicious MSI files signed with fraudulent Authenticode signatures since January 2023. The majority of these downloads are associated with European users.
This disclosure is made as the United States Cybersecurity and Infrastructure Security Agency (CISA). Added Two flaws for known exploited vulnerabilities (KEV) catalog and announced new pilot program This is intended to alert critical infrastructure entities to “vulnerabilities commonly associated with known ransomware exploits.”
Microsoft has also released a number of critical remote code execution flaws affecting the HTTP protocol stack (CVE-2023-23392CVSS score: 9.8), Internet Control Message Protocol (CVE-2023-23415CVSS score: 9.8), and remote procedure call runtime (CVE-2023-21708CVSS score: 9.8).
Other notable mentions include patches for four identified privilege escalation bugs in the Windows kernel, ten remote code execution flaws affecting Microsoft PostScript and PCL6 class printer drivers, and WebView2 Edge browser spoofing vulnerability.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
Microsoft also announced OneDrive for Android (CVE-2023-24882 and CVE-2023-24923CVSS score: 5.5), one spoofing vulnerability in Office for Android (CVE-2023-23391CVSS score: 5.5), one security bypass bug in OneDrive for iOS (CVE-2023-24890CVSS score: 4.3), one privilege escalation issue with OneDrive for macOS (CVE-2023-24930CVSS score: 7.8).
Rounding out the list are patches for two high-severity vulnerabilities in the Trusted Platform Module (TPMs) 2.0 Reference Library Specification (CVE-2023-1017 and CVE-2023-1018CVSS score: 8.8), which can lead to information disclosure and privilege escalation.
Software patches from other vendors
Besides Microsoft, other vendors have released security updates since the beginning of the month to fix several vulnerabilities, including:


