Microsoft has revealed four different ransomware families. KelangerFileCoder, MacRansom, and EvilQuest – these are known to affect Apple macOS systems.
“Though these malware families are old, they demonstrate the range of functionality and malicious behavior possible on the platform,” said the technology giant’s security threat intelligence team. Said in Thursday’s report.
The first vectors in these ransomware families include what the Windows makers call “user-assisted methods.” In this method, the victim downloads and installs a Trojanized application.
Alternatively, it may arrive as a second stage payload dropped by existing malware on an infected host, or as part of a supply chain attack.
Regardless of the tactics employed, attackers rely on legitimate operating system functionality, exploiting vulnerabilities to infiltrate systems and encrypt targeted files.
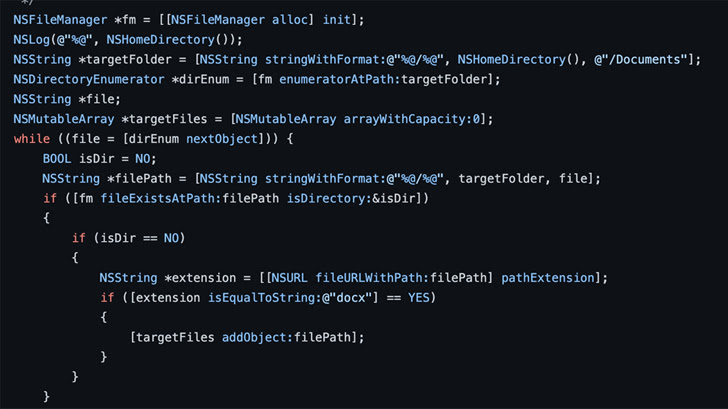
This includes using the UNIX find utility to enumerate files and library functions such as opendir, readdir, and closedir. Another method mentioned by Microsoft, but not employed by ransomware. NSFileManager Objective-C interface.
KeRanger, MacRansom, and EvilQuest have also been observed utilizing a combination of hardware- and software-based checks to determine if malware is running in a virtual environment and attempt to resist analysis and debugging attempts. It has been.
In particular, KeRanger uses a technique known as delayed execution to evade detection. This is achieved by having him sleep for 3 days on startup before launching any malicious functions.
Persistence, which is essential to ensure malware execution across system reboots, is established in the following ways: launch agent When kernel queueMicrosoft pointed out.
FileCoder uses the ZIP utility to encrypt files, while KeRanger uses AES encryption Cipher block chain (CBC) mode to reach the goal. On the other hand, both MacRansom and EvilQuest Symmetric encryption algorithm.
First publicly disclosed in July 2020, EvilQuest goes beyond typical ransomware to include other Trojans such as keylogging, injecting arbitrary code to compromise Mach-O files, and disabling security software. It incorporates features such as
It also has the ability to execute arbitrary files directly from memory, effectively leaving no trace of the payload on disk.
According to Microsoft, “Ransomware continues to be one of the most prevalent and influential threats affecting organizations. We are casting a wider net of targeted targets,” Microsoft said.


