Microsoft on Thursday attributed a flurry of recent ransomware incidents targeting the transportation and logistics sectors of Ukraine and Poland to a threat cluster that overlapped with the Russian government-backed Sandworm group.
An attack revealed last month by the tech giant involved a previously undocumented strain of malware called Prestige, and all victims were said to have occurred within an hour of each other. .
The Microsoft Threat Intelligence Center (MSTIC) currently tracks the threat actor under the element-themed moniker Iridium (formerly DEV-0960), citing overlaps with Sandworm (aka Iron Viking, TeleBots, and Voodoo Bear). increase.
“This attribution assessment is based not only on forensic artifacts, but also on victimology, tradecraft, functionality and infrastructure overlap with known Iridium activity,” MSTIC said. increase. Said with an update.
The company further credited the group with orchestrating a breach targeting many of Prestige’s victims dating back to March 2022, prior to the October 11th ransomware deployment.
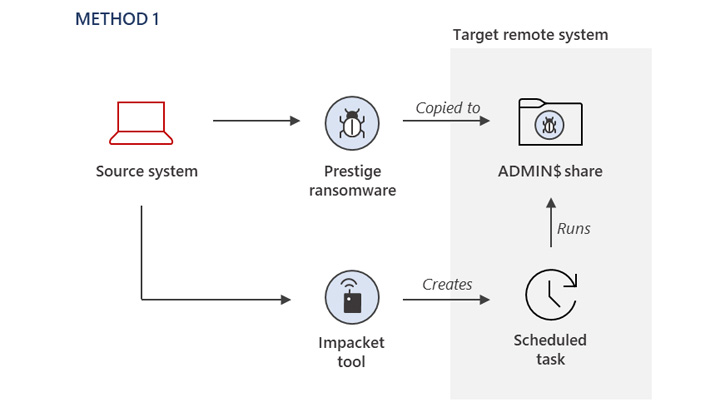
The method of initial compromise remains unknown, although it is suspected that it involved gaining access to the highly privileged credentials required to enable the kill chain.
“The Prestige campaign could highlight a measured change in Iridium’s devastating attack calculations, demonstrating an increased risk to organizations supplying or transporting humanitarian or military aid directly to Ukraine. ” said the company.
This finding comes more than a month after Recorded Future linked another activist group (UAC-0113) with ties to the Sandworm attackers, using a domestic campaign to deliver backdoors to compromised machines. of identifying Ukrainian users by impersonating a telecommunications provider.
In its Digital Defense Report published last week, Microsoft further mentioned Iridium for its pattern of targeting critical infrastructure and operational technology entities.
“Iridium deployed the Industroyer2 malware in an unsuccessful attempt to neutralize millions of people in Ukraine,” said Redmond, adding that the attackers “used phishing campaigns to target organizations inside and outside Ukraine. obtained initial access to the desired accounts and networks of
The development comes amid ongoing ransomware attacks targeting industrial organizations around the world in the third quarter of 2022. Dragos says he has reported 128 such incidents during this period, compared with his 125 in the previous quarter.
“The LockBit ransomware family has accounted for 33% and 35% of all ransomware incidents targeting industrial organizations and infrastructure in the last two quarters, respectively. “Because of that,” says an industrial security company. Said.
Other notable strains observed in Q3 2022 include: Cl0pMedusa Locker, SpartaBianlian, donutOnyx, REvil, and yanluowan.



