The identity of the second attacker behind golden chicken According to cybersecurity firm eSentire, the malware was discovered due to a “fatal” security “fatal mistake.”
The person in question lives in Bucharest, Romania and is known to be codenamed Jack. He is one of his two criminals who runs an account under the name “badbullzvenom” on his Exploit.in forum in Russian, and the other is “Montreal’s It’s Chuck.
eSentire characterized Jack as the true mastermind behind the Golden Chicken. He is also listed as the owner of a vegetable and fruit import-export business, according to evidence unearthed by a Canadian company.
“Like ‘Chuck of Montreal’, ‘Jack’ uses multiple aliases for underground forums, social media and Jabber accounts, and he also goes to great lengths to disguise himself.” eSentire researchers Joe Stewart and Keegan Keplinger said. Said.
“‘Jack’ put a lot of effort into obfuscating the Golden Chicken malware, trying to make it undetectable by most people.” [antivirus] It is aimed at enterprises and strictly allows only a small number of customers to purchase access to Golden Chickens MaaS. ”
Golden Chickens (aka More_eggs) is a malware suite used by financially motivated cybercriminals such as Cobalt Group and FIN6. The attackers behind the malware, also known as Venom Spider, operate under a Malware as a Service (MaaS) model.
This JavaScript malware is distributed through phishing campaigns and comes with several components to collect financial information, perform lateral movement, and even drop a ransomware plugin for PureLocker. Teracrypt.
According to eSentire, Jack’s online activity dates back to 2008. He was just 15 years old at the time and was a novice member of various cybercrime forums. All his aliases are tracked together as LUCKY.
The investigation will compile Jack’s digital trail, tracing Jack’s rise from a teenager interested in building malicious programs to a longtime hacker working on password stealers, crypters, and More_eggs.
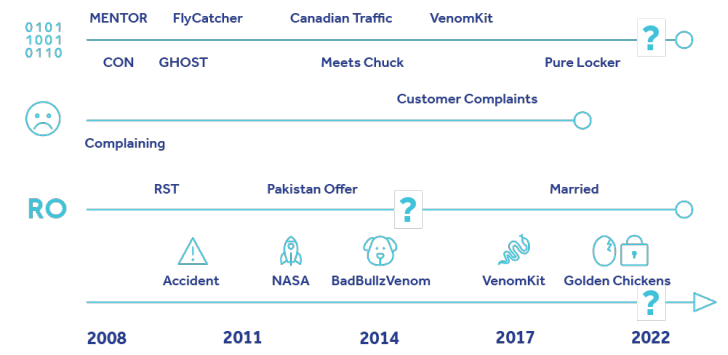
Some of Jack’s early malware tools, developed in 2008, included Voyer, which could collect users’ Yahoo! information. An information stealer named FlyCatcher that can record instant messages and keystrokes.
A year later, Jack released a new password stealer called CON. This password stealer is designed to siphon credentials from various web browsers, VPNs, FTP applications and even now-defunct messaging apps like his MSN Messenger and Yahoo!. Messenger.
Later that same year, Jack began promoting a crypter called GHOST that helped other attackers encrypt and obfuscate malware with the goal of evading detection. It is believed that development of the tool was put on hold in 2010 after his father suddenly died in a car accident.
Way back in 2012, Jack began to earn a reputation as a fraudster within the cybercrime community for failing to provide adequate support to customers who purchased his products.
He also said in a forum post on April 27, 2012, that he was considering moving to Pakistan to work as a security expert in the government, referring to one of Crypta’s customers. A person said, “I work for the Pakistani guv.” [read government].
Zero Trust + Deception: Learn How to Outsmart Attackers!
See how Deception can detect advanced threats, stop lateral movement, and strengthen your Zero Trust strategy. Join us for an insightful webinar!
It’s not immediately clear if Jack ended up going to Pakistan, but eSentire has confirmed that the 2019 campaign conducted by Pakistani attackers known as SideCopy and the first to the More_eggs backdoor. He said he found a tactical overlap with Jack’s VenomLNK malware acting as an access vector.
Jack is suspected of passing by “Chuck of Montreal” between the end of 2012 and October 4, 2013. On this day, a message containing LUCKY-related contact information (Jabber address) was posted by Lampedusa from Chuck’s badbullz account on his forum. .
It is speculated that Jack brokered a deal with Chuck that allowed him to post on various underground forums under Chuck’s aliases of “badbullz” and “badbullzvenom” as a way of avoiding notoriety as the Ripper.
Adding credence to this hypothesis is that one of LUCKY’s new tools, a kit for building macros called MULTIPLIER, was released in 2015 via the badbullzvenom account, while the The fact that the attacker has stopped posting through that handle.
“Using the badbullzvenom and badbullz accounts without the knowledge of forum members allows him to basically start with a clean slate and continue to build credibility under the account aliases badbullz and badbullzvenom. explained the researchers.
Then in 2017 badbullzvenom (aka LUCKY) released another tool called VenomKit. This has since evolved into Golden Chickens MaaS. The malware’s ability to evade detection has also attracted attention. cobalt groupa Russian-based cybercriminal organization that used Cobalt Strike to deploy Cobalt Strike in attacks targeting financial institutions.
Two years later, another financially motivated threat actor named FIN6 (aka ITG08 or Skeleton Spider) was attacked. observed Leverage the Golden Chickens service to anchor intrusions targeting point-of-sale (POS) machines used by European and US retailers.
The cybersecurity firm said it also discovered the identities of his wife, mother and two sisters. He and his wife live in the upmarket district of Bucharest, and his wife’s social media accounts are said to document trips to cities such as London, Paris and Milan. The photos also show them wearing designer clothes and accessories.
“This actor, who goes by the alias LUCKY and shares badbullz and badbullzvenom accounts with Montreal-based cybercriminal ‘Chuck’, made a fatal mistake when using the Jabber account,” the researchers said. said.


