The attackers behind the black hat redirect malware campaign expanded the campaign to infect over 10,800 websites using over 70 fake domains mimicking URL shortening services.
Sucuri researcher Ben Martin said, “The primary goal is ad fraud by artificially increasing traffic to pages containing AdSense IDs, including Google Ads, to generate revenue.” Said In a report released last week.
Details of the malicious activity were first published by the GoDaddy-owned company in November 2022.
The campaign, which is said to have been active since last September, is designed to redirect visitors to a compromised WordPress site to a fake Q&A portal. The purpose seems to be to increase the authority of spam sites in search engine results.
Sucuri said at the time, “These bad guys were probably just trying to convince Google that real people from different IPs, using different browsers, were clicking on search results.” There is potential,” he said. “This technique artificially sends a signal to Google that these pages are performing well in search.”
Bing’s search results links and Twitter’s link shortening feature (t[.]co) services show a growing threat actor footprint, along with Google in redirects.
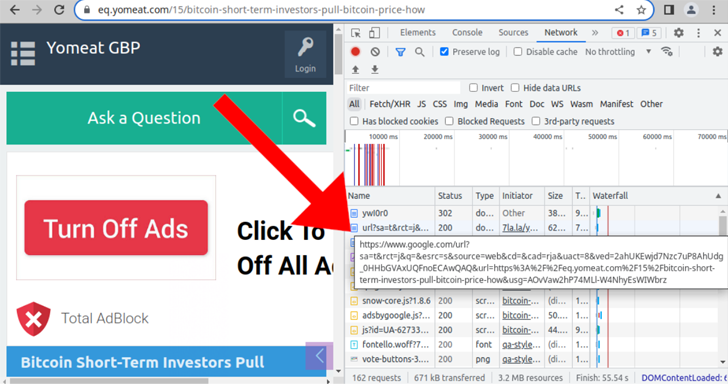
It also uses fake shortened URL domains masquerading as common URL shorteners such as Bitly, Cuttly, and ShortURL, but actually directs visitors to sketchy Q&A sites.
According to Sucuri, the redirect landed on a Q&A site discussing blockchain and cryptocurrencies, whose URL domain is now hosted at DDoS-Guard. DDoS-Guard is a Russian internet infrastructure his provider that has been put under scanners to provide bulletproof hosting services.
“Unnecessary redirects to fake Q&A sites via fake short URLs increase ad impressions, clicks, and revenue for the people behind this campaign,” said Martin. I will explain. “This is him one of a very large and ongoing campaign of organized ad revenue fraud.”
It is not known exactly how WordPress sites get infected in the first place. However, once a website is compromised, attackers can inject backdoor PHP code to allow persistent remote access and redirect of site visitors.
“Additional malware injection The wp-blog-header.php file It runs every time the website is loaded and reinfects the website. This ensures that the environment remains infected until all traces of malware are dealt with. “


