A large-scale attack campaign discovered in the wild is based on Kubernetes (K8s) role-based access control (RBACMore) to create backdoors and run cryptocurrency miners.
“The attackers also deployed a DaemonSet to hijack and hijack the resources of the attacking K8s cluster,” said cloud security firm Aqua. report Share with Hacker News.Israeli company that dubbed the attack RBAC Bustersaid it found 60 exposed K8s clusters exploited by the threat actors behind this campaign.
The attack chain begins with the attacker gaining initial access through a misconfigured API server, then checks the compromised server for evidence of competing minor malware, and uses RBAC to persist. set gender.
“The attacker created a new ClusterRole with almost administrator-level privileges,” the company said. “The attacker then created ‘ServiceAccount’, ‘kube-controller’ in the ‘kube-system’ namespace. Finally, the attacker created a ‘ClusterRoleBinding’ and bound the ClusterRole to her ServiceAccount. created a strong, discreet permanence.”
In an observed intrusion into a K8s honeypot, attackers weaponized exposed AWS access keys, gained a foothold in environments, stole data, and attempted to escape cluster boundaries.
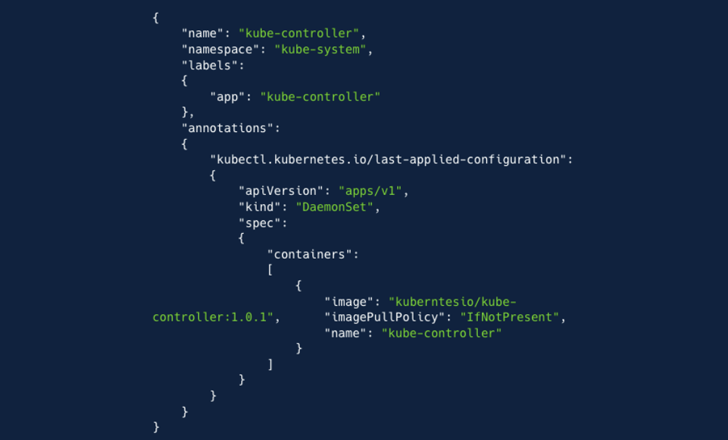
The final step in the attack required the threat actor to create a DaemonSet to deploy a Docker-hosted container image (“kuberntesio/kube-controller:1.0.1”) to all nodes. A container that has been pulled by him 14,399 times since it was uploaded five months ago harbors a cryptocurrency miner.
Zero Trust + Deception: Learn How to Outsmart Attackers!
See how Deception can detect advanced threats, stop lateral movement, and strengthen your Zero Trust strategy. Join us for an insightful webinar!
“The container image named ‘kuberntesio/kube-controller’ is an example of typosquatting impersonating a legitimate ‘kubernetesio’ account,” said Aqua. “This image is a key component of the control plane, the popular ‘kube-controller-manager’ container that runs inside his Pods on every master node and is responsible for detecting and responding to node failures. It also mimics the image.”
Interestingly, some of the tactics described in this campaign are similar to another illegal cryptocurrency mining operation that also utilized DaemonSets to create Dero and Monero. It is not clear at this time if the two sets of attacks are related.


