Iranian nation-state hacking group known as oil rig continues to target government agencies in the Middle East as part of a cyber espionage campaign that uses new backdoors to steal data.
Trend Micro researchers Mohamed Fahmy, Sherif Magdy and Mahmoud Zohdy said: Said.
While the technique itself is not unprecedented, it is the first time OilRig has employed it in their strategy, demonstrating the continual evolution of techniques to circumvent security protections.
The Advanced Persistent Threat (APT) group, also known as APT34, Cobalt Gypsy, Europium, and Helix Kitten, documented Targeted phishing attacks have been occurring in the Middle East since at least 2014.
The group, affiliated with Iran’s Ministry of Information and Security (MOIS), used backdoors such as Karkoff, Shark, Marlin, and Saitama to steal information in recent attacks in 2021 and 2022, and varied its operations. known to use a powerful toolset.
The starting point of the latest activity is a .NET-based dropper tasked with delivering four different files, including a main implant (“DevicesSrv.exe”) that steals specific files of interest.
Also used in the second stage is a dynamic link library (DLLs) file that can collect credentials from domain users and local accounts.
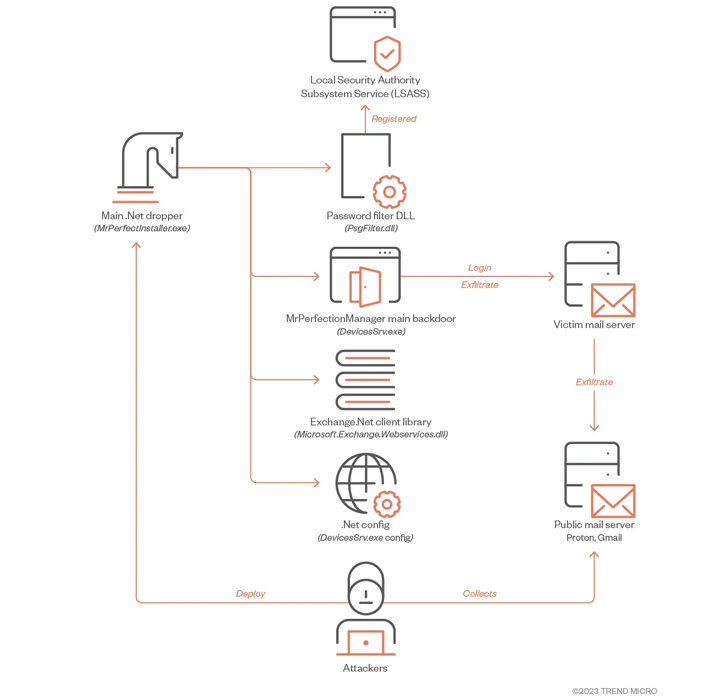
The most notable aspect of the .NET backdoor is its exfiltration routine, which involves sending electronic documents to attacker-controlled email Gmail and Proton Mail addresses using stolen credentials.
“Threat actors use valid accounts with stolen passwords to relay these emails through government exchange servers,” said the researchers.
The campaign’s connection to APT34 stems from similarities between the first-stage dropper and Saitama, victim patterns, and the use of internet-connected exchange servers as a communication method observed in the case of Karkoff.
If anything, the growing number of malicious tools associated with OilRig is a testament to attackers creating new malware based on the target environment and privileges possessed during specific stages of an attack. shows flexibility.
“Despite the simplicity of the routine, the novelty of the second and final stages shows that this entire routine is just one part of a larger campaign targeting governments,” the researchers said. says.


