The Iranian nation-state group known as the muddy water It has been observed performing destructive attacks in hybrid environments under the guise of ransomware operations.
This is because new research from the Microsoft Threat Intelligence team has found that threat actors are targeting both on-premises and cloud infrastructure, dubbed another new activity cluster. DEV-1084.
“Threat actors attempted to disguise this activity as a standard ransomware campaign, but the irreversible action indicates that destruction and chaos were the ultimate goal of the operation.” clearly Friday.
MuddyWater is the name assigned to an Iran-based actor that the US government has publicly tied to the country’s Ministry of Information and Security (MOIS). At least he is known to have been active since 2017.
It has also been tracked by the cybersecurity community under various names such as Boggy Serpens, Cobalt Ulster, Earth Vetala, ITG17, Mercury, Seedworm, Static Kitten, TEMP.Zagros and Yellow Nix.
Cybersecurity company Secureworks Cobalt Ulster Profileit is not at all uncommon in the realm of threat actors to “insert false flags into code related to their operations” as a distraction in attempts to disrupt attribution efforts.
The attacks launched by this group primarily target Middle Eastern countries, and over the past year we have observed intrusions leveraging the Log4Shell flaw to compromise an Israeli entity.
According to Microsoft’s latest findings, the attackers likely worked with DEV-1084 to carry out the spying attack. The latter carried out destructive actions after MuddyWater successfully gained a foothold in the targeted environment.
“Before handing over access to DEV-1084, Mercury likely exploited a known vulnerability in an unpatched application for initial access, performed extensive reconnaissance and discovery, and We established a network, moved laterally across the network, and often waited weeks, sometimes months, before moving on to the next stage,” Microsoft said.
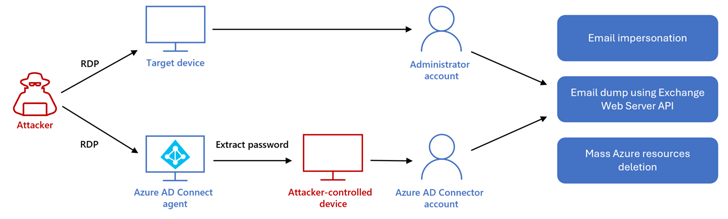
In activity detected by Redmond, DEV-1084 then exploited the compromised highly privileged credentials to encrypt on-premises devices, including server farms, virtual machines, storage accounts, and virtual networks. You performed a large-scale deletion of cloud resources.
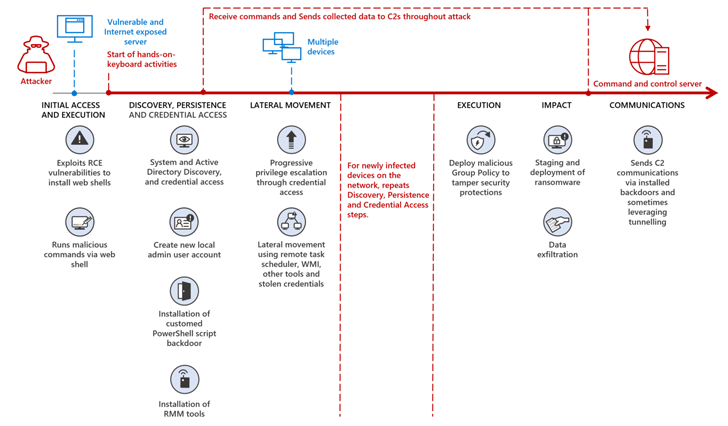
Additionally, the attacker gained full access to an email inbox via Exchange Web Services and used it to perform “thousands of search activities” to target an unnamed high-ranking employee. Spoofed messages sent to internal and external recipients.
The aforementioned actions take place between 12:38 AM (when the attacker logs into the Microsoft Azure environment via compromised credentials) and 3:21 AM (when the attacker attempts another parties).
where DEV-1084 is same threat actor or assumption The ‘DarkBit’ persona was used in February as part of a ransomware and extortion attack targeting Technion, a leading research university in Israel. The Israeli National Cyber Directorate last month said: Attribution Attack on Muddywater.
Learn How to Secure Your Identity Perimeter – A Proven Strategy
Improve your business security in our upcoming expert-led cybersecurity webinar: Exploring Identity Perimeter Strategies!
“DEV-1084″ […] It has established itself as a criminal interested in extortion as an attempt to obfuscate Iranian links and strategic motives to the attack,” Microsoft added.
The link between Mercury and DEV-1084 stems from overlapping infrastructure, IP addresses, and tools, the latter being observed using reverse tunneling utilities. rigolothe classic MuddyWater artifact.
That said, is DEV-1084 operating independently of MuddyWater and cooperating with other Iranian actors, or is it a sub-team that is summoned only when needed to carry out destructive attacks? There is not enough evidence to judge
Earlier last year, Cisco Talos described MuddyWater as a “conglomerate” of several smaller clusters rather than a single cohesive group. The appearance of DEV-1084 suggests a nod in this direction.
“Though these teams appear to operate independently, they are often used for Iranian national security purposes, such as espionage, intellectual theft, and subversive or subversive activities based on targeted victims. We are motivated by the same factors along the way,” Talos said in March 2022.


