Ransomware attacks are a major problem for any organization, and the severity of this problem continues to intensify.
Recently, Microsoft’s incident response team investigated the BlackByte 2.0 ransomware attack, revealing the frightening speed and damaging nature of these cyberattacks.
The findings show that hackers can complete the entire attack process from gaining initial access to causing significant damage in just five days. They waste no time to infiltrate your system, encrypt your important data and demand ransom money to release it.
This shortened schedule poses significant challenges for organizations trying to protect themselves from these harmful operations.
BlackByte ransomware is used in the final stage of the attack, encrypting data using an 8-digit numeric key.
To carry out these attacks, hackers use a powerful combination of tools and techniques. Investigation revealed that they were using an unpatched Microsoft Exchange Server. This approach has proven to be very successful. Exploitation of this vulnerability provides initial access to the target network and sets the stage for malicious activity.
This ransomware further employs process haloing and antivirus evasion strategies to ensure successful encryption and avoid detection.
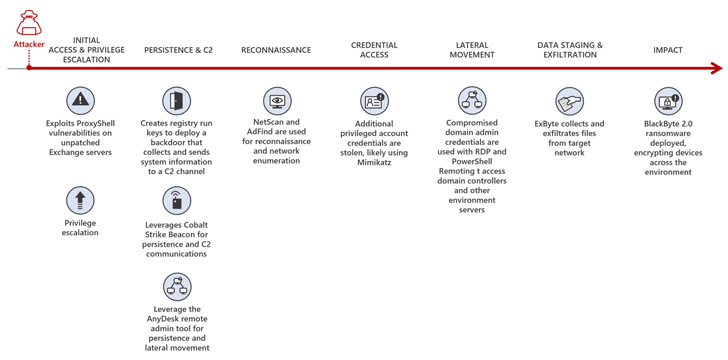
Additionally, the web shell allows remote access and control, allowing you to maintain your presence within the compromised system.
of report He also emphasized the deployment of Cobalt Strike Beacons to facilitate command and control operations. These advanced tools give attackers a wide range of skills and make it more difficult for organizations to defend against them.
🔐 Privileged Access Management: Learn How to Overcome Key Challenges
Discover different approaches to overcoming the challenges of privileged account management (PAM) and leveling up your privileged access security strategy.
In addition to these tactics, the research also uncovered several other bad practices used by cybercriminals. They utilize “live off the land” tools to blend in with legal processes and escape detection.
This ransomware modifies volume shadow copies on infected machines to prevent data recovery through system restore points. Attackers also deploy specially crafted backdoors to give them continued access after the initial compromise.
An alarming surge in ransomware attacks requires immediate action by organizations around the world. Based on these findings, Microsoft provided some actionable recommendations.
Organizations are primarily required to implement robust patch management procedures and apply critical security updates in a timely manner. Enabling tamper protection is another important step as it hardens your security solution against malicious attempts to disable or bypass it.


