The car’s mobile app could have allowed the hackers to remotely unlock the car, turn the engine on and off, and honk the horn.
These are the findings of security researcher and bug bounty hunter Sam Curry, who has investigated vulnerabilities that could affect Hyundai, Genesis, Nissan, Infiniti, Honda and Acura vehicles, among others.
Curry and his colleagues first turned their attention to the official mobile app used by owners of Hyundai and Genesis vehicles. This app allows authenticated users to start, stop, lock and unlock a car.
and series of tweetsCurry exploited vulnerabilities in Hyundai’s apps and APIs to bypass authentication checks, remotely unlock vehicles simply by knowing the owner’s email address, and eventually complete account takeover. We have shown how to achieve
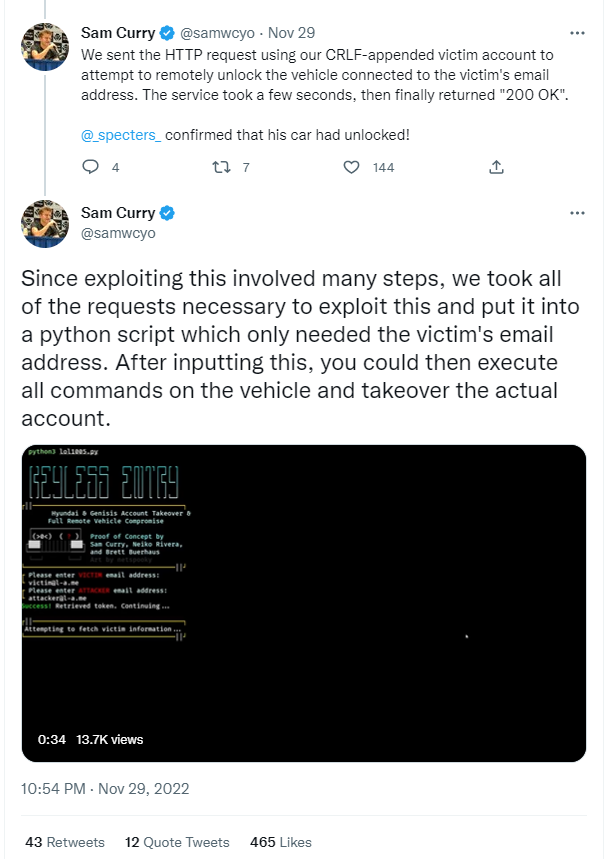
Later it became clear that the same risk existed for owners of Genesis vehicles.
Curry responsibly disclosed the security issue to Hyundai and Genesis.
A Hyundai spokesperson said: The Record “With the exception of the Hyundai vehicle and the researcher’s own account, our investigation did not reveal that anyone else had access to the customer’s vehicle or account as a result of the issues raised…”
It’s a relief, I think. However, the fact that the security risk existed in the first place remains a major concern.
Perhaps encouraged by discoveries related to Hyundai and Genesis vehicles, Curry continued to investigate vulnerabilities affecting other manufacturers, particularly those utilizing the Sirius XM Connected Vehicle Services telematics platform. .
like Callie has now explained An unauthorized third party could send commands to Nissan, Infiniti, Honda, and Acura vehicles simply by knowing the vehicle identification number (VIN).
Currie also discovered that even if a particular car isn’t actively subscribing to SiriusXM’s service, it can be registered for the service simply by knowing the VIN, which is usually visible through the car’s windshield.
You can use this technology to remotely stop or start your car, lock or unlock it, flash your headlights or honk your horn. Even the owner’s private information (name, phone number, address, car information) can be extracted without permission.
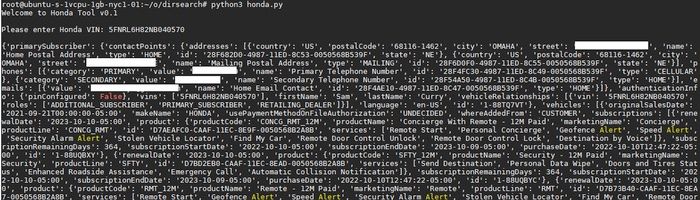
And while the telematics service’s API calls worked even if the user didn’t have an active SiriusXM subscription, Curry said vehicle owners were free to register or register from the service.
Luckily, Curry, a responsible security researcher, was able to privately notify interested parties of the issue and patch the vulnerability before the details were made public.
Apps make life easier for drivers,
reduce security.I just hope the manufacturer will put it in
Future efforts to ensure connectivity with smartphones
the car is better protected


