Malicious attackers use voice phishing (vishing) tactics to trick victims into installing Android malware on their devices. research ThreatFabric reveals.
A Dutch mobile security firm said it had identified a network of phishing websites targeting online banking users in Italy designed to obtain contact details.
A social engineering technique known as telephone directed attack delivery (TOAD) uses information previously collected from fraudulent websites to call victims.
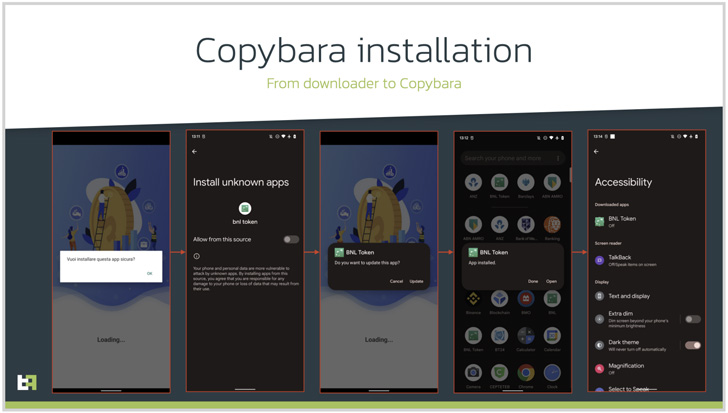
A caller posing as a bank support agent tells the caller to install a security app with extensive privileges, when in reality it is intended to gain remote access or behavior. Malicious software. financial fraud.
In this case, it leads to the deployment of dubbed Android malware. Kopibarais a mobile Trojan that was first detected in November 2021 and is primarily used to carry out on-device fraud via overlay attacks targeting users in Italy. Copybara has also been confused with another malware family known as BRATA.
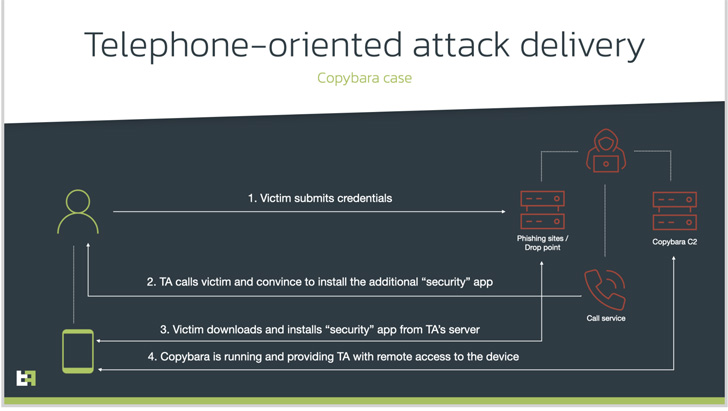
ThreatFabric estimates that the TOAD-based campaigns started around the same time, indicating that the activity has been going on for almost a year.
Like other Android-based malware, Copybara’s RAT functionality is enhanced by abusing operating system accessibility service APIs to gather sensitive information and uninstall downloader apps to reduce its forensic footprint. .
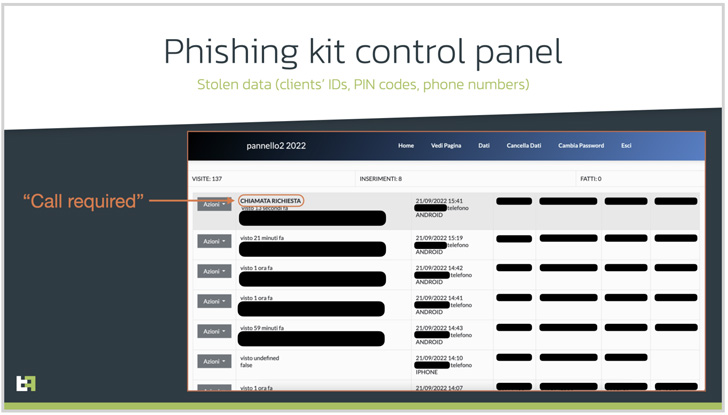
Additionally, the infrastructure utilized by the attackers includes a second piece of malware named SMS Spy that allows adversaries to access all incoming SMS messages and intercept one-time passwords (OTPs) sent by banks. has been found to deliver
The new wave of hybrid fraud attacks offers scammers a new dimension to launch compelling Android malware campaigns that have relied on traditional methods such as Google Play store droppers, deceptive ads, and smishing. increase.
“Such an attack requires more resources. [threat actors’] Threatfabric’s Mobile Threat Intelligence (MTI) team told Hacker News.
“Unfortunately, I would also like to point out that targeted attacks have been more successful in terms of fraud success, at least in this particular campaign.”
This is not the first time TOAD tactics have been employed to orchestrate banking malware campaigns. Last month, MalwareHunterTeam Detailed A similar attack targeted customers of India-based bank Axis Bank, attempting to install an information-stealing program masquerading as a credit card rewards app.
“All suspicious calls should be double-checked by calling the financial institution,” the MTI team said, adding, “Financial institutions provide customers with knowledge of ongoing campaigns and develop mechanisms to detect suspicious activity. We need to harden the client apps that have it,” he added.




