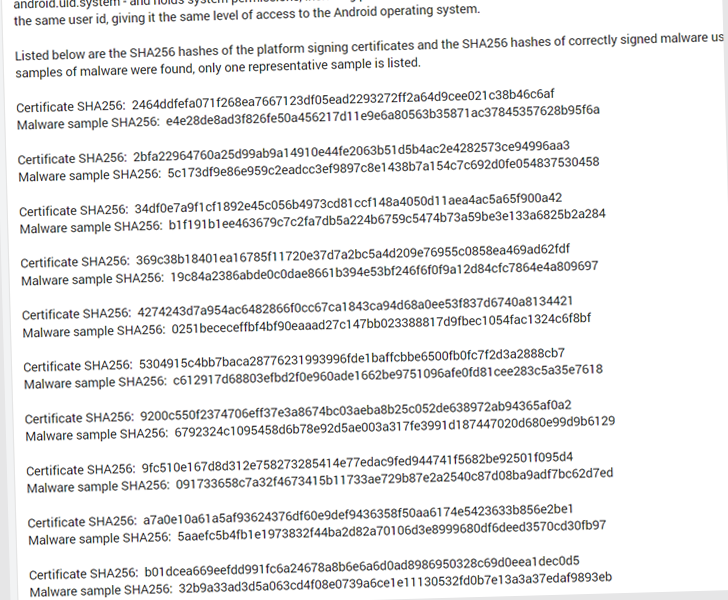
Platform certificates used by Android smartphone vendors such as Samsung, LG, and MediaTek are known to be abused to sign malicious apps.
Findings first discover and report Created by Google Reverse Engineer Łukasz Siewierski on Thursday.
Android Partner Vulnerability Initiative (AVPI) read.
“The ‘Android’ application runs under a highly privileged user ID (android.uid.system) and has system permissions, including permissions to access user data. “
This effectively means that a rogue application signed with the same certificate can obtain the highest level of privileges as the Android operating system, allowing it to collect all kinds of sensitive information from compromised devices.
Below is a list of malicious Android app packages that abuse certificates.
- com.russian.signato.renewis
- com.sledsdffsjkh.Search
- com.android.power
- com.management.propaganda
- com.sec.android.musicplayer
- com.houla.quicken
- com.attd.da
- com.arlo.fappx
- com.metasploit.stage
- com.vantage.electronic.cornmuni
However, it is not immediately clear where and how these artifacts were discovered, or whether they were used as part of an active malware campaign.
A search on VirusTotal reveals that the identified samples are flagged by antivirus solutions as HiddenAds adware, Metasploit, information stealers, downloaders, and other obfuscated malware.
When asked for comment, Google has notified all affected vendors to rotate their certificates and said it has no evidence that these apps were distributed through the Play Store.
“Our OEM partners took immediate mitigation measures when key compromises were reported,” the company said in a statement to Hacker News. “End users are protected by user mitigations implemented by OEM partners.”
“Google has implemented extensive malware detection in the Build Test Suite that scans system images. Google Play Protect also detects malware. There is no indication that this malware is or was on the Google Play Store. As always, we advise our users to: Make sure you’re running the latest version of Android.”



