New research has found that attackers can abuse legitimate functionality of GitHub Codespaces to deliver malware to victims’ systems.
GitHub codespace is a cloud-based, configurable development environment that enables users to debug, maintain, and commit changes to a specific codebase from a web browser or via Visual Studio Code integration.
It also provides port forwarding capabilities that allow web applications running on specific ports in your codespace to be accessed directly from your browser on your local machine for testing and debugging purposes.
“Manually forward ports, label forwarded ports, share forwarded ports with members of your organization, share forwarded ports publicly, or add forwarded ports to codespace You can also add it to your configuration.” GitHub I will explain in that document.
this is important Note that exposed forwarded ports also allow anyone who knows the URL and port number to view the running application without authentication.
Additionally, GitHub Codespaces uses HTTP for port forwarding. If a publicly visible port is updated to use HTTPS, or removed and re-added, the port’s visibility automatically changes to private.
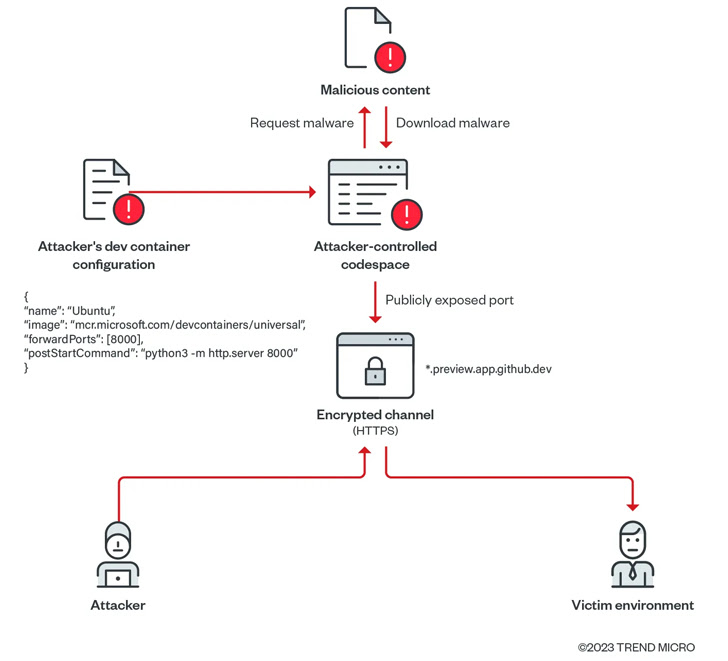
Cyber Security Company Trend Micro found Such publicly shared forwarded ports can be abused to create malicious file servers using GitHub accounts.
“In the process, these exploited environments will not be flagged as malicious or suspicious, even if they serve malicious content (scripts, malware, ransomware, etc.), and organizations will We may consider these events harmless or false positives,” the researchers said. said Nitesh Surana and Magno Logan.
In a proof-of-concept (PoC) exploit demonstrated by Trend Micro, an attacker creates a codespace, downloads malware into an environment from an attacker-controlled domain, sets the visibility of forwarded ports to public, An application that acts as a web server that hosts payloads.
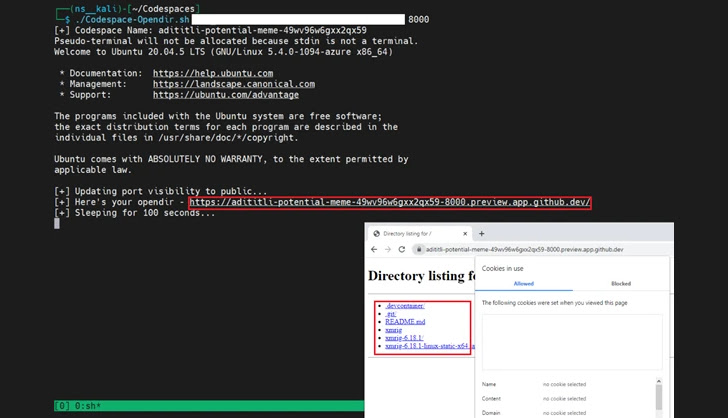
To make matters worse, attackers can extend this method to deploy malware and compromise the victim’s environment. This is because each codespace domain associated with an exposed port is unique and less likely to be flagged as malicious by security tools.
“Using such scripts, attackers can exploit GitHub Codespaces to rapidly serve malicious content by exposing ports in the codespace environment,” the researchers explained. I’m here.
While this technique has not yet been observed in the wild, the findings are a reminder of how attackers can weaponize cloud platforms for profit and to carry out a range of illegal activities.
“Cloud services offer benefits for both legitimate users and attackers,” conclude the researchers. “The capabilities offered to legitimate subscribers will also be available when using resources provided by threat actors. [cloud service provider].”


