Actors associated with the Gootkit malware have made “significant changes” to their toolset, adding new components and obfuscations to their infection chain.
Mandiant, owned by Google, monitoring Activity cluster under the moniker UNC2565note that the use of malware is “only for this group”.
Gootkit, also known as Gootloader, uses a technique known as search engine optimization (SEO) poisoning to trick victims into visiting them while searching for business-related documents such as contracts and agreements. spread through compromised websites.
The suspicious document comes in the form of a ZIP archive containing JavaScript malware that, when launched, paves the way for additional payloads such as Cobalt Strike Beacon, FONELAUNCH, and SNOWCONE.
FONELAUNCH is a .NET-based loader designed to load encoded payloads into memory, and SNOWCONE is a downloader that performs the task of retrieving the next-stage payload (usually IcedID) over HTTP. .
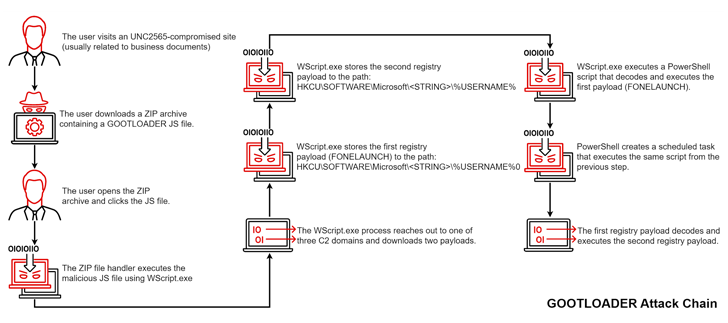
While Gootkit’s overarching goals have not changed, the attack sequence itself has been significantly updated, including trojanizing a JavaScript file in a ZIP archive and including another obfuscated JavaScript file. resulting in malware execution.
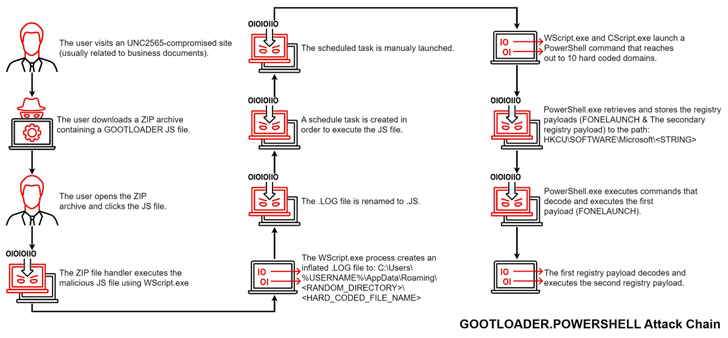
A new variant discovered by a threat intelligence firm in November 2022 is tracked as GOOTLOADER.POWERSHELL. It is worth noting that the improved infection chain was documented by Trend Micro earlier this month, detailing a Gootkit attack targeting the Australian healthcare sector.
Additionally, malware authors use three different approaches to hide Gootkits, including hiding the code within modified versions of legitimate JavaScript libraries such as jQuery, Chroma.js, and Underscore.js to evade detection. is said to have taken
Gootkit is not alone. Three different flavors of FONELAUNCH, FONELAUNCH.FAX, FONELAUNCH.PHONE and FONELAUNCH.DIALTONE, will be used by UNC2565 to execute DLLs, .NET binaries and PE files from May 2021. I was. The malware arsenal is continuously maintained and updated.
“These changes demonstrate the active development and feature growth of UNC2565,” said Mandiant researchers Govand Sinjari and Andy Morales.


