A zero-day vulnerability in Internet Explorer was actively exploited by North Korean threat actors, using recent vulnerabilities to target South Korean users. Itaewon Halloween Crowd Crush Trick users into downloading malware.
The discovery, reported by Google Threat Analysis Group researchers Benoît Sevens and Clément Lecigne, scar craftAPT37, InkySquid, Reaper, and Ricochet Chollima.
“The group has historically targeted South Korean users, North Korean defectors, policy makers, journalists and human rights activists,” TAG said. Said Analysis on Thursday.
New research indicates that threat actors continue to exploit Internet Explorer flaws such as CVE-2020-1380 and CVE-2021-26411 to create backdoors such as BLUELIGHT and Dolphin. The latter was made public late last month by Slovak cybersecurity firm ESET.
Another important tool in its arsenal is RokRat, a Windows-based remote access Trojan with extensive functionality that allows it to capture screenshots, log keystrokes, and even collect Bluetooth device information. I have it.
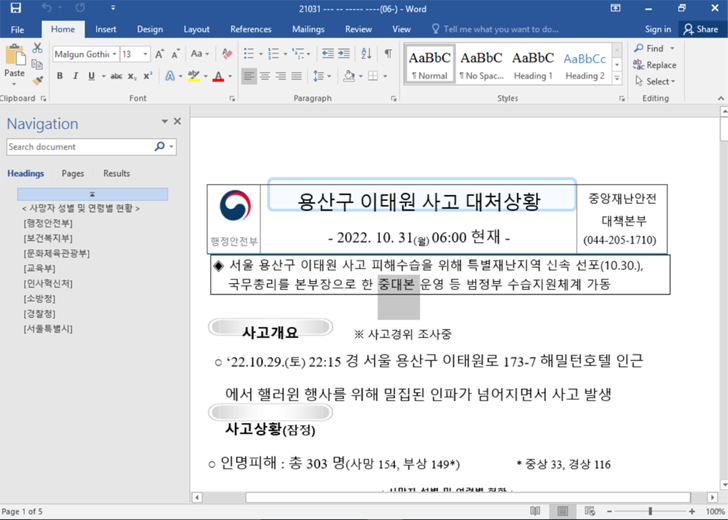
The attack chain observed by Google TAG involves the use of malicious Microsoft Word documents. Upload to VirusTotal October 31, 2022. It exploits a zero-day vulnerability in Internet Explorer, CVE-2022-41128, in the JScript9 JavaScript engine that Microsoft patched last month.
The file references the October 29th incident in Seoul’s Itaewon district, and uses public interest in this tragedy to retrieve exploits for vulnerabilities when the file is opened. This attack is made possible by the fact that Office uses Internet Explorer to render HTML content.
A successful exploit delivers a shellcode that wipes all traces by clearing Internet Explorer’s cache and history and downloading the next stage payload.
Google TAG says it was unable to recover subsequent malware used in the campaign, but is suspected to have been involved in deploying RokRat, BLUELIGHT, or Dolphin.



