Google Cloud revealed last week that it has identified 34 different hacked release versions of its Cobalt Strike tool. shipped November 2012.
According to the Google Cloud Threat Intelligence (GCTI) team’s findings, versions span from 1.44 to 4.7 and add up to 275 unique JAR files in total. The latest version of Cobalt Strike is version 4.7.2.
Cobalt Strike developed by Fortra (formerly HelpSystems) is a popular adversarial framework used by red teams to simulate attack scenarios and test the resilience of cyber defenses.
It consists of a Team Server acting as a command and control (C2) hub for remotely expropriating infected devices, and a stager (reporting to C2) designed to deliver next-stage payloads called beacons. fully functional implants). server.
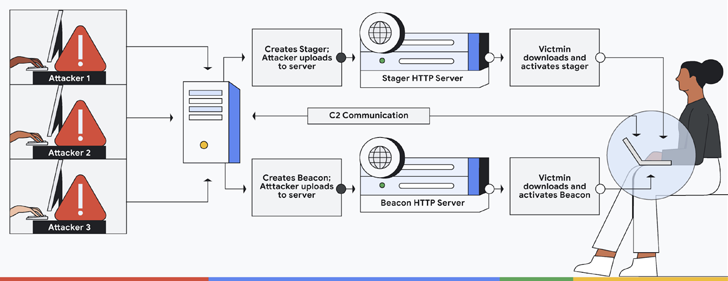
Given its extensive feature suite, malicious versions of the software are increasingly being weaponized by many threat actors to further their post-exploitation activities.
“Although the intent of Cobalt Strike is to emulate a real-world cyberthreat, malicious actors have leveraged its capabilities to initiate lateral movement in the victim’s network as part of their second stage attack payload. We use it as a robust tool to do that,” said Greg. Sinclair, a reverse engineer for his Chronicle subsidiary of Google, said: Said.
To tackle this exploit, GCTI has developed a series of Open source YARA rules To flag various variants of software used by malicious hacking groups.
The aim, Sinclair said, is to “remove the bad versions while leaving the legitimate versions untouched.” It’s about making it harder,” he added.


