New Android Malware Strain Named Gordawson has been detected in the official Google Play Store, across 60+ legitimate apps that have been downloaded over 100 million times in total.
An additional 8 million installs are tracked through ONE Store, South Korea’s leading third-party app storefront.
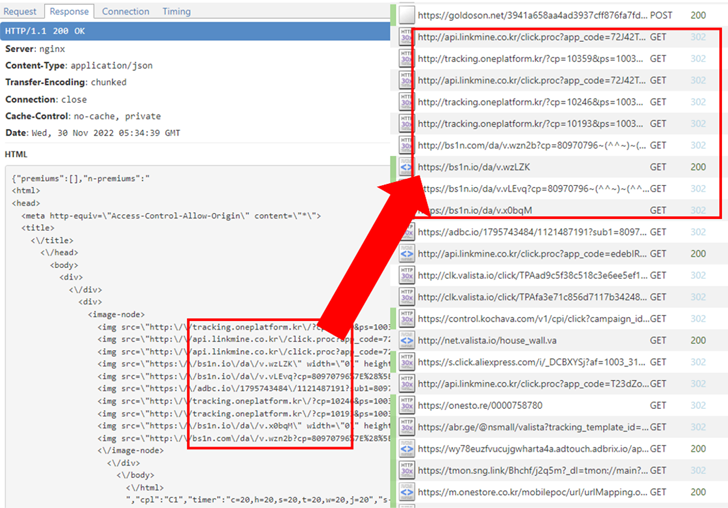
The rogue component is part of a third-party software library used by the app in question and is able to collect information about installed apps, Wi-Fi and Bluetooth connected devices, and GPS locations.
“Furthermore, the library has the ability to carry out ad fraud by clicking ads in the background without user consent,” said SangRyol Ryu, a security researcher at McAfee. Said In a report released last week.
It also includes the ability to covertly load web pages, which can be abused to load advertisements for financial gain. hide HTML code WebView Direct traffic to a URL.
Following responsible disclosure to Google, 36 of the 63 offending apps were removed from the Google Play store. The rest of his 27 apps have been updated to remove malicious libraries.
Prominent apps include −
- L.POINT with L.PAY
- Swipe Brick Breaker (removed)
- money manager expenses and budget
- TMAP – 대리, 주차, 전기차충전, 킥보드를티맵에서!
- I’m sorry
- Jeongyeon – Genie
- business[컬쳐캐쉬]
- rubber player
- 메가박스 (removed), and
- live score, real time score
The findings highlight the need for app developers to be transparent about the dependencies used in their software. It goes without saying that we take appropriate measures to protect your information from such misuse.
Kern Smith, Vice President of Sales Engineering, Americas, Zimperium, said:
“The use of third-party SDKs and code, and the possibility of introducing malicious code into other legitimate applications, has led attackers to start targeting the software supply chain to gain the largest possible footprint. We continue to grow because we are.”
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – join us for this expert-led webinar!
The development follows Cyble’s release of what it calls a new Android banking Trojan. chameleon It has been active since January 2023 and targets users in Australia and Poland.
This Trojan abuses Android’s accessibility services to collect credentials and cookies, log keystrokes, prevent uninstallation, and perform other malicious activities, which is why it has been found in the wild. It’s no different than any other banking malware out there.
It is also designed to display malicious overlays on top of certain app lists, intercept SMS messages, and have unused functionality that allows it to download and execute another payload.
Chameleon, as its name suggests, tends to evade by building in anti-emulation checks to detect if the device is rooted or running in a debug environment, and terminates itself if so. increase.
To mitigate such threats, users should download apps only from trusted sources, scrutinize app permissions, use strong passwords, enable multi-factor authentication, and send emails from unknown senders. We recommend that you exercise caution when receiving SMS and emails.


