When there’s a lot of bad news in the world of cybersecurity, it’s always good to share positive stories.
Researchers at cybersecurity firm Unit 221B have revealed that they have been covertly helping Zeppelin ransomware victims crack their computer systems since 2020.
Since its emergence in 2019, Zeppelin ransomware victims have included corporations, critical infrastructure organizations, defense contractors, educational institutions, and the healthcare and medical industry.
While it typically demands ransoms in the $50,000 range (some have demanded ransoms in excess of $1 million), Zeppelin leaves business cards next to the encrypted files.
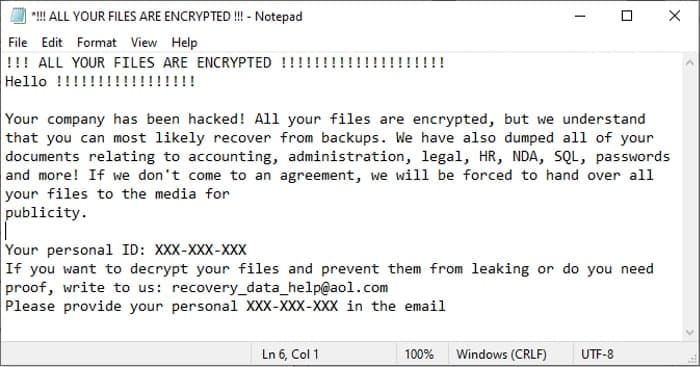
Your company has been hacked! All files are encrypted, but I understand that they can most likely be restored from backups. We also dumped all documents related to accounting, administration, legal, HR, NDA, SQL, passwords, etc! If no agreement is reached, we will be forced to hand over all files to the media for publicity .
Boffin in unit 221B zeppelin ransomware It then targeted charities, nonprofits, and even homeless shelters. It’s clear that all of these establishments deserve more money than the blackmailer’s pocket.
Alternatively, a blog post on the Unit 221B website eloquently states:
General rules of thumb for Unit 221B offices are:
“Don’t [REDACTED] With the homeless and the sick! It simply triggers ADHD in us and puts us into hyperfocus mode, which is good if you’re a good guy, but not so good if you’re an asshole. ”
Unit 22B researchers discovered a vulnerability in Zeppelin’s encryption flow that temporarily left keys in the registry. For full details on how Unit 221B discovered the flaw and used it to crack the victim’s computer locks, visit technical blog post on the company’s website.
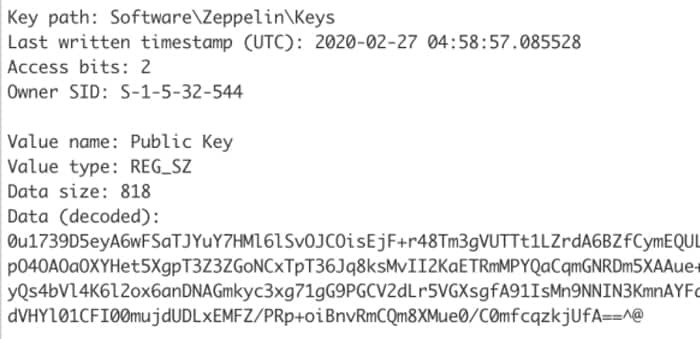
The net result was that the researchers were able to extract the key by creating a decryption tool that victims could run on their infected system. The keys were then uploaded to a considerable amount of computing power (his 20 servers donated by Digital Ocean (each with 40 CPUs for him)) and eventually he spent 6 hours Encryption keys are cracked after huff and puff.
This is an impressive achievement and helped an organization that was in dire need of help after the Zeppelin ransomware attack.
What also impressed me was that the researchers knew that bragging about their work would only reach the ears of the ransomware gangs using Zeppelin, so it was easier for the researchers to keep their discoveries alive. It was a secret. exposed to even greater risk.
Unit 221B chose to disclose details of its activities after the Zeppelin casualties were significantly reduced. The tool is still freely available and should work against the latest versions of Zeppelin.
Researchers credit Cylance security experts for their work. Work before analyzing Zeppelinhosted the massive Digital Ocean to provide computing power, and the developers of CADO-NFS to help the project.
Did you find this article interesting? Follow Graham Cluley on Twitter Also Mastodon To read more about the exclusive content we post.


