in-depth analysis of FIN7 debunked the organizational hierarchy of cybercrime syndicates and revealed their role as affiliates in launching ransomware attacks.
We also uncovered a deeper connection between this group and the larger threat ecosystem comprised of the now-defunct DarkSide, REvil, and LockBit families of ransomware.
The highly active threat group, also known as Carbanak, has added ransomware to its strategy and set up fake security firms to lure researchers into carrying out ransomware attacks. Known for using a wide range of tools and tactics to expand the ‘horizon’. Penetration testing guise.
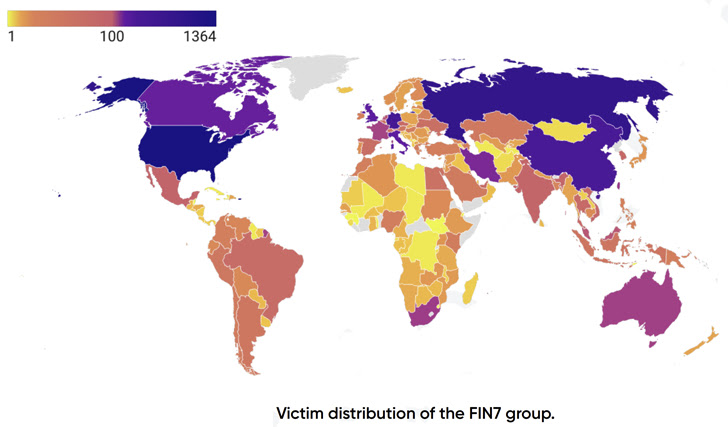
Over 8,147 victims worldwide have been compromised by financially motivated attackers, mostly in the US Other prominent countries include China, Germany, Canada, Italy, and the UK
Over the years, FIN7’s intrusion techniques have diversified beyond traditional social engineering to include infected USB drives, compromising software supply chains, and using stolen credentials purchased from underground markets.
“Today, the first approach is to carefully pick high-value companies from a pool of already-compromised corporate systems and either force them to pay large ransoms to restore their data, or steal their data and remote access for profit. It’s all about finding unique ways to personalize,” said PRODAFT. Said In a report shared with The Hacker News.
According to a Swiss cybersecurity firm, Russian-speaking hacking crews have weaponized several flaws in Microsoft Exchange, including CVE-2020-0688, CVE-2021-42321, ProxyLogon, and ProxyShell, to gain access to targeted environments. It has also been confirmed that they are gaining a foothold.
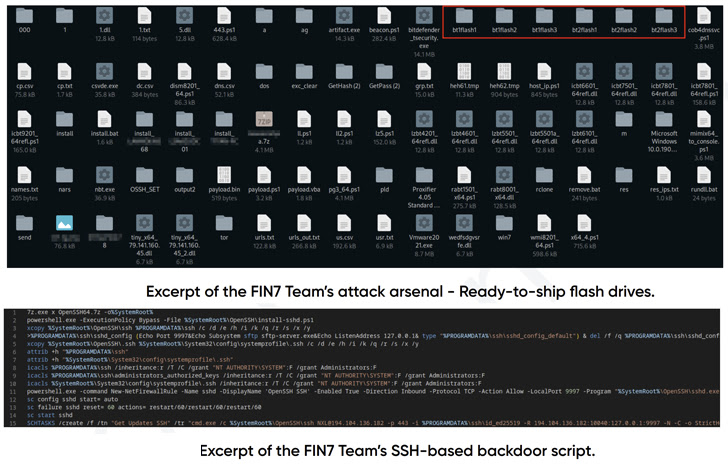
Despite the use of double extortion tactics, the attacks staged by the group deployed SSH backdoors into compromised systems, even in scenarios where the victim had already paid the ransom.
The idea highlights attempts to resell access to other ransomware organizations and retarget victims to maximize profits with minimal effort as part of an illegal money-making scheme. Yes, of course, annual revenue, founding date, and number of employees.
This “demonstrates a particular type of feasibility study that is seen as a unique behavior among cybercriminal groups,” the researchers said.
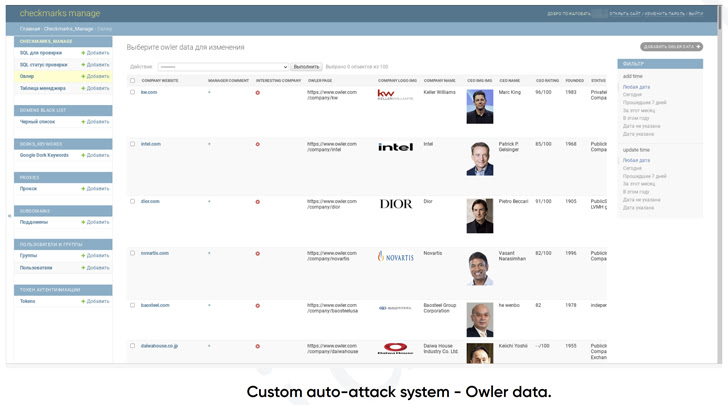
In other words, the FIN7 modus operandi looks like this: We use services like Crunchbase, Dun & Bradstreet (DNB), Owler, and Zoominfo to nominate companies and organizations with the highest revenue. He also uses other of his website analytics platforms such as MuStat and Similarweb to monitor traffic to the victim’s site.
Initial access is then obtained via one of many intrusion vectors, followed by data extraction, file encryption, and finally a ransom amount determined based on the company’s earnings.
These infectious sequences are Carbanak, Lizar (aka Tirion), and icebotThe latter was first documented in January 2022 by the Gemini Advisory owned by Recorded Future.
Other tools developed and provided by FIN7 include a module called Checkmarks for automating mass scanning of vulnerable Microsoft Exchange servers and other public web applications, and Cobalt Strike after exploitation.
In another sign that criminal groups are functioning like traditional corporations, FIN7 follows a team structure consisting of top-level management, developers, pentesters, affiliates, and a marketing team. , each with a separate responsibility.
Two members named Alex and Rash are the main players behind the operation, while a third managing member named Sergey-Oleg delegates duties to other associates of the group and oversees its execution. responsible for
However, an examination of the group’s Jabber conversation history shows that operators in managerial positions use coercion and intimidation to threaten team members to work more, issue ultimatums, and “resign or take responsibility.” If you escape, you will hurt your family.”
The findings come more than a month after cybersecurity firm SentinelOne identified a potential link between FIN7 and the Black Basta ransomware operation.
According to PRODAFT, “FIN7 has established itself as a highly versatile and well-known APT group targeting enterprise companies.” It’s about scouring companies based on information from the industry and identifying the most profitable targets.”
“Although they have internal problems related to the unequal distribution of their acquired financial resources and somewhat questionable practices towards their members, they have managed to establish a strong presence in the cybercrime arena. ”



