New attack campaigns have targeted the gaming and gambling sector since at least September 2022. ICE London 2023 Gaming industry trade show event scheduled for next week.
Israeli cybersecurity company security jaws Tracking an activity cluster with the name ice breakersays the intrusion uses sophisticated social engineering tactics to deploy a JavaScript backdoor.
The attack sequence proceeds as follows. The attacker poses as a customer in starting a conversation with her agent at the game website support, prompting the individual to open a screenshot image hosted on her Dropbox.
security jaws Said The attacker is “fully aware of the fact that customer service is run by humans.”
Clicking on a malicious link sent in chat retrieves a VBScript file as a LNK payload or backup option. The VBScript file is configured to download and run an MSI package containing a Node.js implant.
The JavaScript file contains all the functionality of a typical backdoor, allowing an attacker to enumerate running processes, steal passwords and cookies, steal arbitrary files, take screenshots, remotely It can even run VBScript imported from the server and open a reverse proxy on the compromised server. host.
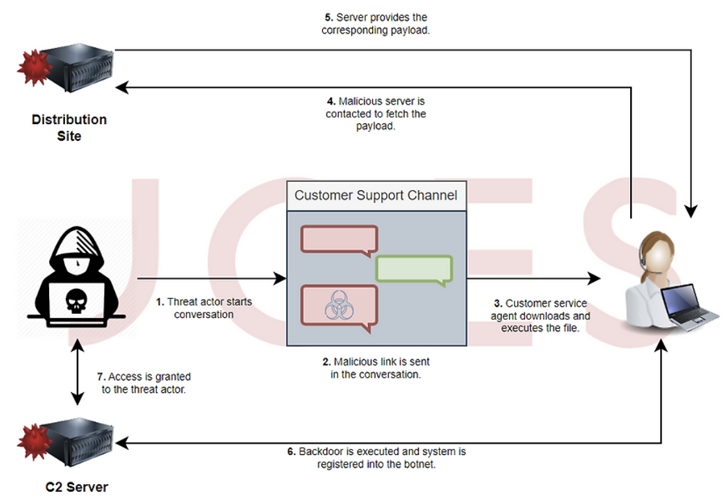
If the VBS downloader is executed by the victim, the infection will eventually lead to: Houdiniis a VBS-based remote access Trojan dating back to 2013.
The attacker’s origin is currently unknown, but he has been observed using broken English while conversing with a customer service agent. Some of the indicators of compromise (IOCs) associated with the campaign are: previously shared By MalwareHunterTeam in October 2022
Felipe Duarte, senior threat researcher at Security Joes, said:
“Analyzing unprecedented compiled JavaScript second-stage malware is extremely complex, and we know that we are dealing with skilled threat actors that may be sponsored by profit holders. is showing.”


