Infamous Emotet Malware return after a short breakis currently being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems.
Associated with threat actors tracked as Gold Crestwood, Mummy Spider, or TA542, Emotet continues to be a powerful and resilient threat despite removal attempts by law enforcement.
a derivative of krydex banking worm – Which continue exchanged By Dridex around the same time GameOver Zeus was discontinued in 2014 – Emotet evolved “It becomes a monetized platform for other threat actors to run malicious campaigns in a pay-per-install (PPI) model, enabling theft of sensitive data and extortion of ransoms.”
Emotet infection conduit The return in late 2021 was facilitated by TrickBot to deliver Cobalt Strike, IcedID, Qakbot, Quantum ransomware, and TrickBot.
“Emotet is known for long periods of inactivity when the botnet maintains a steady state but does not deliver spam or malware, often occurring several times a year,” said Secureworks. says. Note in the actor’s profile.
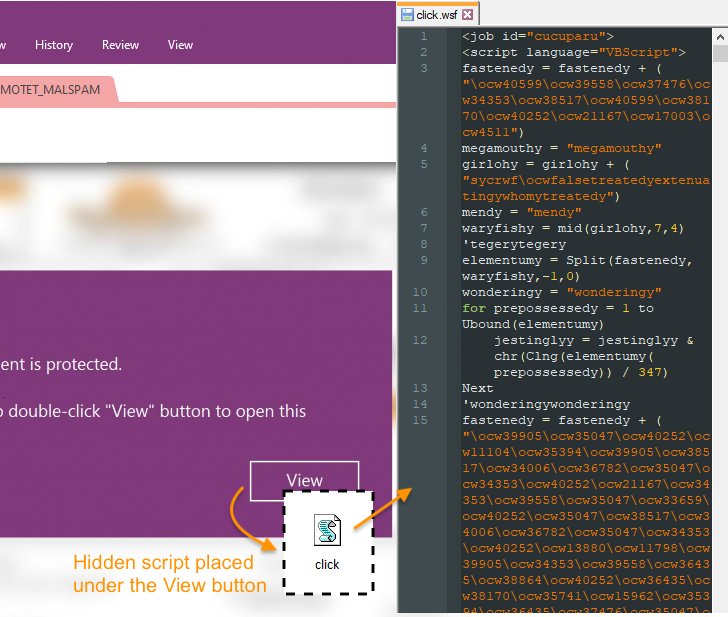
Dropper malware is usually distributed through spam emails that contain malicious attachments. But with Microsoft taking steps to block macros in downloaded Office files, OneNote attachments are emerging as an attractive alternative.
“OneNote files are simple, but effective against social engineering users with fake notifications that the document is protected,” said Malwarebytes. disclosed with a new alert. “[表示]When instructed to double-click a button, the victim inadvertently double-clicks the embedded script file. ”
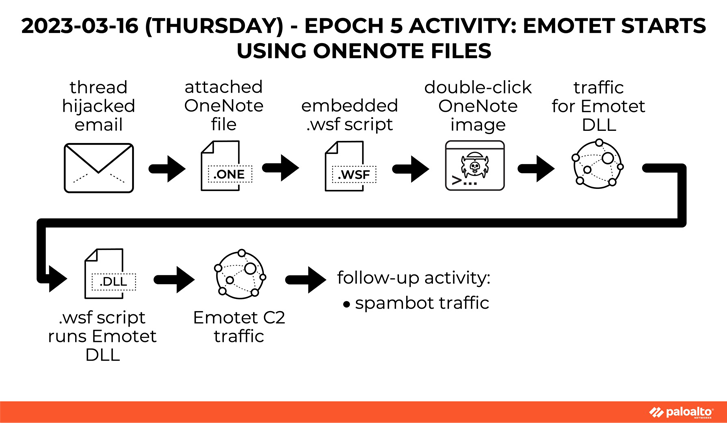
A Windows Script File (WSF) is designed to retrieve and execute an Emotet binary payload from a remote server. A similar finding found that Cybulle, IBM X-Forceand Palo Alto Networks unit 42.
That said, Emotet continues to deliver malicious payloads using booby-trap documents containing macros, lures users with social engineering lures, and enable macros to fuel its attack chain. Let
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
According to multiple reports from , such documents utilize a technique called decompression bombs to hide very large files (over 550 MB) inside ZIP archive attachments, allowing them to fly under the radar. is observed. Cybulle, deep instinct, HornetSecurityand trend micro.
this is, padding 00 bytes At the end of the document, we artificially inflate the file size to exceed the limits imposed by anti-malware solutions.
The latest developments demonstrate operator flexibility and agility in switching attachment types on first delivery to evade detection signatures. It also attacker Use OneNote document Distributes a wide range of malware including AsyncRAT, Icedid, RedLine Stealer, Qakbot, XWorm.
according to TrellixIn 2023, the majority of malicious OneNote detections were reported in the United States, South Korea, Germany, Saudi Arabia, Poland, India, United Kingdom, Italy, Japan, and Croatia, with manufacturing, high-tech, telecommunications, finance, and energy has emerged as a top target sector.


