A new variant of the notorious Dridex banking malware has set its sights on Apple’s macOS operating system using a previously undocumented infection method, according to the latest research.
Armando Nathaniel Pedragoza, a researcher at Trend Micro, said: “We adopted a new technique to deliver documents with embedded malicious macros to users without masquerading as invoices or other business-related files.” says. Said in a technical report.
Dridex, also known as Bugat or Cridex, is an information-stealing program known to collect sensitive data from infected machines and distribute and execute malicious modules. This is due to an electronic crime group known as Evil Corp (aka Indrik Spider).
This malware is also believed to be the successor to Gameover Zeus, which itself is a sequel to another banking Trojan called Zeus. His previous Dridex campaigns targeting Windows leveraged macro-enabled Microsoft Excel documents sent via phishing emails to deploy payloads.
European and American organized law enforcement operations interrupted In October 2015, the botnet was attacked and a Moldovan citizen named Andrey Ghinkul was arrested for his role as an administrator of the operation. In December 2018, Ginkle declared After his extradition in February 2016, pending service by a U.S. federal court.
Subsequently, in December 2019, the U.S. Treasury Department Sanctions imposed Evil Corp announced a $5 million bounty for its two principal members, Maksim Yakubets and Igor Turashev. Despite these efforts, Dridex continues to evolve and prove to be a resilient threat.
Analysis of the Dridex sample by Trend Micro included: Mach First submitted to VirusTotal in April 2019. Since then, 67 more artifacts have been found in the wild, some of which are from his December 2022.
Artifact contains malicious embedded document – first detected Dating back to 2015. auto open macro It runs automatically when you open a Word document.
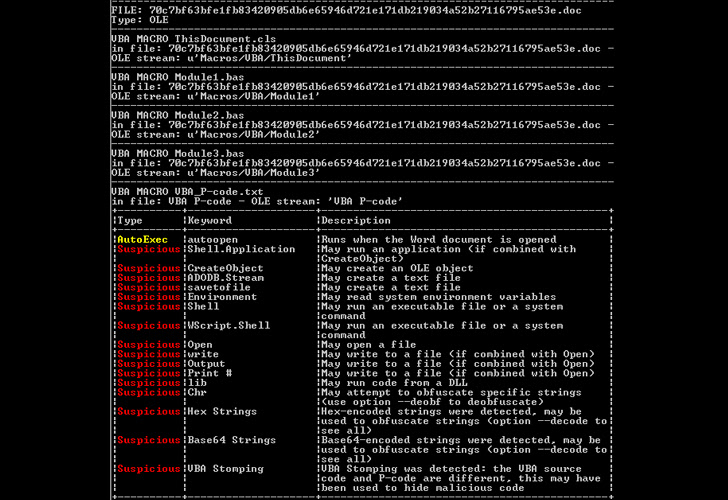
In addition, the Mach-O executable searches for all “.doc” files in the current user directory (~/User/{username}) and extracts malicious files copied from the embedded document in hexadecimal format. It is designed to be overridden with some macro code. Throw away.
“Microsoft Word’s macro functionality is disabled by default, but the malware overwrites all document files for the current user, including clean files,” Pedragoza explains. “This makes it difficult for users to determine whether a file is malicious or not, because the file does not come from an external source.”
Macros included in the overwritten document are designed to connect to remote servers and retrieve additional files. It contains a Windows executable that does not run on macOS, indicating a possible attack chain in progress. The binary then attempts to download her Dridex loader onto the compromised machine.
Documents containing booby-trapped macros are typically delivered through social engineering attacks, but the findings suggest that Microsoft’s decision to block macros by default has encouraged attackers to refine their tactics and find more efficient methods of entry. It indicates that you were encouraged to do so.
“At this time, this Dridex variant has minimal impact on macOS users as the payload is an .EXE file (and is therefore not compatible with macOS environments),” Trend Micro said. I’m here. “However, it still overwrites document files that are carriers of Dridex’s malicious macros.”


