Cybersecurity researchers have discovered a previously undocumented payload associated with Romanian actors. Dicottcould launch a distributed denial of service (DDoS) attack.
“Dicott’s name means a lot. Romanian Organized Crime and Counter-Terrorism Police Force“Cado Security” Said in technical reports. “In addition, deliverables from the group’s campaigns include messages and images related to this organization.”
Diicot (née Mexals) was first documented by Bitdefender in July 2021 using a Go-based SSH brute forcer tool called Diicot Brute to compromise Linux hosts as part of a cryptojacking campaign. became clear.
And in early April this year, Akamai revealed what it called a “resurrection” of its 2021 activity, which allegedly began around October 2022, and claimed to have made about $10,000 in illicit profits from this act.
“The attackers use long chains of payloads before finally dropping the Monero cryptominer,” said Akamai researcher Stiv Kupchik. Said at the time. “New features include use of the Secure Shell Protocol (SSH) worm module, improved reporting, improved payload obfuscation, and a new LAN spreader module.”
According to Cado Security’s latest analysis, the group said: CayocinA malware family that shares characteristics with , Qbot and Mirai.
This development demonstrates the threat actor’s ability to launch DDoS attacks. Other activities carried out by this group include exposing rival hacker groups and relying on his Discord for command and control and data theft.
“The deployment of this agent targeted routers running OpenWrt, a Linux-based embedded device operating system,” said the cybersecurity firm. “The use of Cayosin demonstrates Dicot’s willingness to carry out a variety of attacks (not just cryptojacking) depending on the type of target it encounters.”
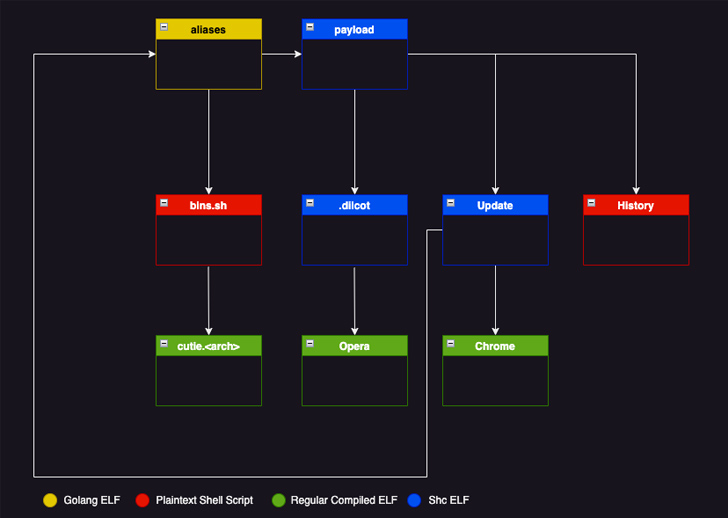
Diicot’s compromise chain remains largely consistent, leveraging custom SSH bruteforce utilities to gain a foothold and drop additional malware such as Mirai variants and cryptominers.
Some of the other tools that actors use are:
- chromium – A Zmap-based internet scanner that can write operation results to a text file (“bios.txt”).
- update – An executable that fetches and runs SSH brute forcers and Chrome if they are not present on the system.
- history – A shell script designed to run Update
SSH brute forcer tools (aka aliases) parse Chrome’s text file output to compromise each identified IP address and, if successful, establish a remote connection to that IP address.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join us for an insightful webinar!
It then runs a series of commands to profile the infected host and use it to deploy a cryptominer or act as a spreader if the machine’s CPU has less than 4 cores.
To mitigate such attacks, we recommend that organizations implement SSH hardening and firewall rules to restrict SSH access to specific IP addresses.
“This campaign specifically targets SSH servers exposed to the Internet with password authentication enabled,” Cado Security said. “The list of usernames and passwords they use is relatively limited and includes default credentials and easily guessed credential pairs.”



