threat actors behind DDoSia The attack tool has developed a new version that incorporates a new mechanism to get a list of targets to attack and bring down junk HTTP requests.
An updated variant, written in Golang, “implements an additional security mechanism to hide the list of targets. This mechanism [command-and-control] Dear Users, Cybersecurity Company Sekoia Said in technical articles.
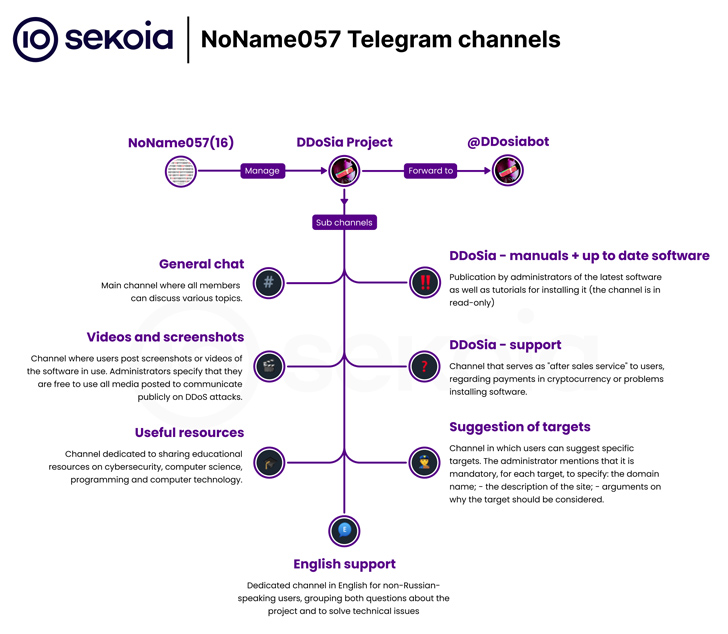
DDoSia is believed to be from a pro-Russian hacker group called DDoSia. No Name (057) 16. Released in 2022, successor bobik botnetthe attack tool is design It launches distributed denial of service (DDoS) attacks against targets primarily located in Europe, Australia, Canada, and Japan.
From May 8 to June 26, 2023, Lithuania, Ukraine, Poland, Italy, Czech Republic, Denmark, Latvia, France, United Kingdom, and Switzerland emerged as the most targeted countries. A total of 486 different websites were affected.
Python and Go-based implementations of DDoSia have been discovered to date, making it a cross-platform program that can be used across Windows, Linux, and macOS systems.
“DDoSia is a multi-threaded application that performs denial-of-service attacks against target sites by repeatedly issuing network requests,” SentinelOne explained An analysis published in January 2023 states that “DDoSia issues requests as directed by a configuration file that the malware receives from its C2 server upon launch.”
DDoSia is distributed through a fully automated process on Telegram, allowing individuals to register for the crowdsourcing effort in exchange for a cryptocurrency payment and a ZIP archive containing the attack toolkit.
What’s notable about the new version is the use of encryption to hide the attack surface list. This indicates that this tool is actively maintained by the operator.
“NoName057(16) strives to make the malware compatible with multiple operating systems. This almost certainly reflects their intent to make the malware available to a large number of users. and, as a result, target a wider range of victims,” Sequoia said.
The development comes after the US Cybersecurity and Infrastructure Security Agency (CISA) warned of targeted denial of service (DoS) and DDoS attacks against multiple organizations in multiple sectors.
“These attacks can waste organizations time and money, and can negatively impact reputations while resources and services are inaccessible,” the agency said. Said Breaking news.
CISA did not provide additional details, but the warning overlaps with the US allegations. Anonymous Sudan The company announced on its Telegram channel that it has closed the websites of the Departments of Commerce, the Social Security Administration (SSA) and the Treasury Department’s Electronic Federal Tax Payment System (EFTPS).
Anonymous Sudan made headlines last month for his Layer 7 DDoS attacks against various Microsoft services, including OneDrive, Outlook, and the Azure web portal. The tech giant tracks the cluster under the name Storm-1359.
The hacker group claimed to be conducting cyberattacks from Africa on behalf of oppressed Muslims around the world. But cybersecurity researchers believe this is a pro-Kremlin operation that has nothing to do with Sudan or members of the hacktivist group KillNet.
In an analysis published on June 19, 2023, Australian cybersecurity vendor CyberCX said: Distinctive calling this organization a “smoke screen for Russian interests”. The company’s website was then rendered inaccessible and visitors were shown a “403 Forbidden” message. The attacker has claimed responsibility for the cyberattack.
In a message posted on June 22, 2023, Anonymous Sudan said, “Reason for attack: Stop spreading rumors about us, tell the truth, stop the investigation we call the dog investigation. I have to,” he said.
Anonymous Sudan, Bloomberg report Last week, he further denied any links between the country and Russia, but acknowledged that the two countries share similar interests and pursue “anything that is hostile to Islam.”
CISA’s latest recommendations have also attracted attention, with the group issuing a statement on June 30, 2023, stating, “A small group in Sudan with limited capabilities has attacked the world’s I forced the disclosure of.” ”


