Remote access Trojans such as StrRAT and Ratty are distributed as a combination of polyglots and malicious Java archives (jar.
“Attackers are currently using polyglot techniques to confuse security solutions that do not properly validate the JAR file format,” said Simon Kenin, security researcher at Deep Instinct. Said in the report.
Multilingual file A file that combines the syntax of two or more different formats so that each format can be parsed without error.
One such 2022 campaign spotted by a cybersecurity firm is deploying StrRAT payloads using JAR and MSI formats (i.e. files that are valid as both JAR and MSI installers). This also means that the file can be run by both Windows and the Java Runtime Environment (JRE), depending on how the file is interpreted.
Another example uses CAB and JAR polyglots to deliver both Ratty and StrRAT. Artifacts are propagated using URL shortening services such as cutt.ly and rebrand.ly, some of which are hosted on Discord.
“What’s special about ZIP files is that they are identified by the presence of a .zip file. end of central directory record It’s at the end of the archive,” Kenin explained.
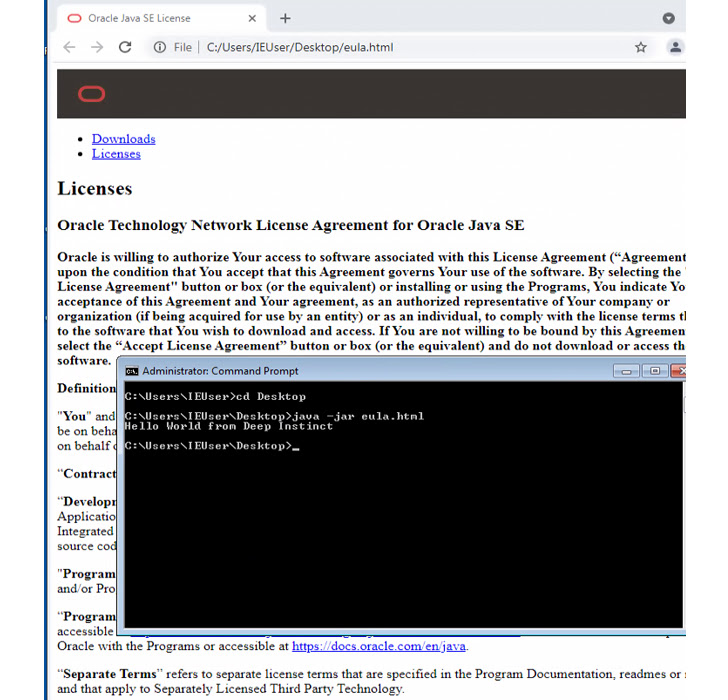
JAR files are not properly validated, creating a scenario where additional malicious content bypasses security software and remains undetected until executed on a compromised host.
This is not the first time such malware-laden polyglots have been detected in the wild. In November 2022, his Berlin-based DCSO CyTec will Strela stealer It’s spread as a DLL/HTML polyglot.
“Proper detection of JAR files should be both static and dynamic,” Kenin said. “It is not efficient to scan all files for the existence of the tail of the central directory record at the end of the file.”
“A defender should monitor both the ‘java’ and ‘javaw’ processes. If such a process has “-jar” as an argument, the filename passed as an argument should be treated as a JAR file, regardless of file extension or Linux output. “File” command. “


