Fortinet’s currently patched zero-day exploit of a medium-severity security flaw Fort iOS The operating system is linked to a suspected Chinese hacking group.
Mandiant, a threat intelligence firm citing sources, said Activity Cluster was part of a broader campaign designed to deploy backdoors into Fortinet and VMware solutions and maintain persistent access to victims’ environments. said to be part.
Google-owned threat intelligence and incident response firm tracks malicious operations under unclassified names UNC3886China-related threat actors.
“UNC3886 is a sophisticated cyber espionage group that is unique in how it operates on its network and in the tools it uses in its campaigns,” said Mandiant researchers. Said in technical analysis.
“UNC3886 has been confirmed to target firewall and virtualization technologies that do not support EDR. The ability to manipulate firewall firmware and exploit zero-days is a deeper level understanding of such technologies. It shows that we have curated the
Note that the adversary was previously associated with another intrusion set targeting VMware ESXi and Linux vCenter servers as part of a hyperjacking campaign designed to drop backdoors such as VIRTUALPITA and VIRTUALPIE. please.
The latest disclosure from Mandiant leverages a zero-day bug in Fortinet’s FortiOS software to cause data loss, OS and file corruption, allowing government agencies and large organizations to fall prey to an unknown attacker. This is due to the fact that it was made clear that
Vulnerabilities tracked as CVE-2022-41328 (CVSS score: 6.5) is for a path traversal bug in FortiOS that could lead to the execution of arbitrary code. Patched by Fortinet on March 7, 2023.
According to Mandiant, attacks launched by UNC3886 targeted Fortinet’s FortiGate, FortiManager, and FortiAnalyzer appliances and deployed two different implants, including THINCRUST and CASTLETAP. This was possible because the FortiManager device was exposed to the internet.
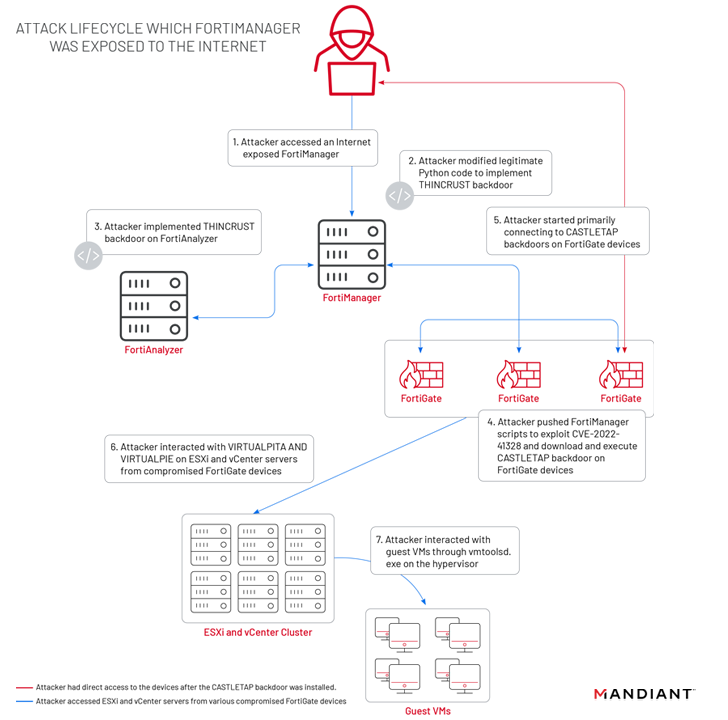
THINCRUST is a Python backdoor that can read and write files on disk as well as execute arbitrary commands.
The persistence provided by THINCRUST is then leveraged to deliver FortiManager scripts that overwrite legitimate files and modify firmware images, armed with FortiOS path traversal flaws.
It contains a newly added payload called ‘/bin/fgfm’ (called CASTLETAP). It beacons an attacker-controlled server to accept incoming instructions that allow it to execute commands, fetch payloads, and extract data from a compromised server. host.
“Once CASTRETAP was deployed on the FortiGate firewall, the attackers connected to ESXi and vCenter machines,” the researchers explained. “Attackers deployed her VIRTUALPITA and her VIRTUALPIE to establish persistence and allow continued access to the hypervisor and guest machines.”
Alternatively, on FortiManager devices implementing Internet access restrictions, an attacker could pivot from a FortiGate firewall compromised with CASTLETAP to drop a reverse shell backdoor named REPTILE (“/bin/klogd”) into the network management system. and is said to have regained access. .
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
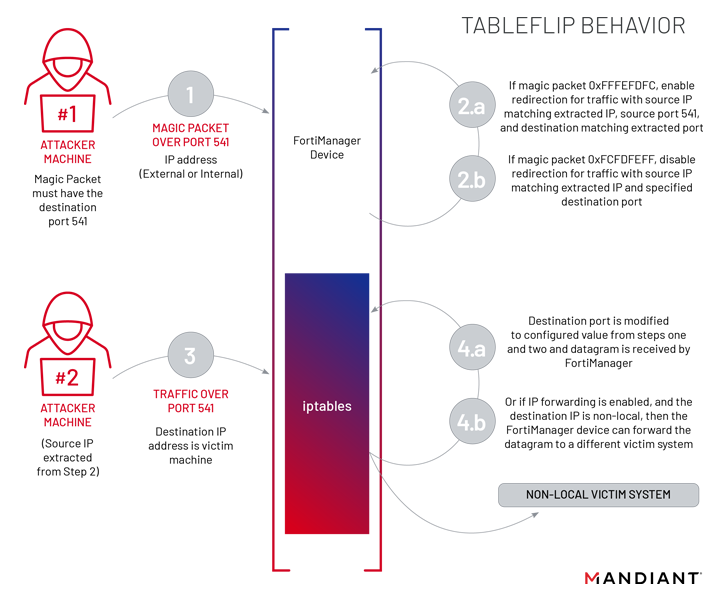
Also employed by UNC3886 at this stage is a utility called TABLEFLIP. This is network traffic redirection software for direct connections to FortiManager devices regardless of access control lists (ACLs) rules have been put in place.
This is not the first time Chinese adversaries have targeted network equipment to distribute bespoke malware. Recent attacks have taken advantage of other vulnerabilities in Fortinet and SonicWall devices.
It is also evident that attackers are developing and deploying exploits at an unprecedented rate. Within seven days of disclosure, he has exploited up to 28 vulnerabilities. Rapid7.
This is important. Notably, hacking crews aligned with China are “particularly adept” at exploiting zero-day vulnerabilities, deploying custom-his malware to steal user credentials, and maintaining long-term access to targeted networks. This is because
“activity […] This is further evidence that advanced cyber espionage actors are utilizing all available techniques to persist and traverse target environments, especially those that do not support EDR solutions.” said Mandiant.


