A previously undocumented Android malware campaign has been observed using a money lending app to blackmail victims into paying with personal information stolen from their devices.
Mobile security company Zimperium dubbed the activity. money mongerpoint out the use of Cross-platform Flutter framework develop an app.
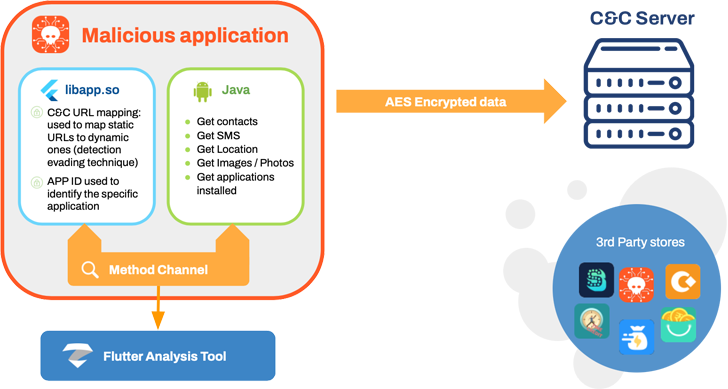
MoneyMonger “utilizes the Flutter framework to obfuscate malicious functionality and complicate detection of malicious activity through static analysis,” Zimperium researchers Fernando Sanchez, Alex Calleja, and Matteo Favaro , and Gianluca Braga said. Said In a report shared with Hacker News.
“The nature of Flutter hides malicious code and activity behind a framework outside the static analysis capabilities of traditional mobile security products.”
The campaign, which is believed to have been active since May 2022, is part of an earlier, broader effort. disclosed By Indian cybersecurity company K7 Security Labs.
None of the 33 apps used in the malicious scheme were distributed through the Google Play store. Instead, money lending applications are available from unofficial app stores or sideloaded onto mobile phones via smishing, compromised websites, deceptive advertising, or social media campaigns.
Once installed, this malware poses risks as it is designed to urge users to give intrusive permissions under the pretext of guaranteeing loans and collect various personal information.
Collected data (GPS locations, SMS, contacts, call history, files, photos, voice recordings, etc.) is used as a pressure tactic to coerce victims into paying excessively high interest rates on loans. increase. The loan will be repaid.
Worse, threat actors can harass borrowers by exposing their information, threatening to make calls from their contact list, or send abusive messages or distorted photos from infected devices. increase.
The scale of the campaign is unknown due to the use of sideloading and third-party app stores, but it is estimated that the malicious app was downloaded over 100,000 times through distribution channels.
Zimperium Director of Mobile Threat Intelligence Richard Melick said in a statement:
“Quick loan programs are full of predatory models such as high interest rates and repayment schemes, but adding blackmail to the equation increases the level of malice.”
Findings will be published two weeks after Lookout discovered Nearly 300 mobile loan applications have been downloaded on Google Play and Apple’s App Store, totaling over 15 million downloads, and have been found to be involved in looting.
These apps not only steal huge amounts of user data, but also come with hidden fees, high interest rates, and payment terms that strongly arm victims for fraudulent loan payments.
Late last month, Lookout “exploited victims’ desire for quick cash to trick borrowers into predatory loan agreements and demand that they be granted access to sensitive information such as contacts and SMS messages.” said.
developing countries prime number Target Digital lending is experiencing explosive growth in markets such as India, and people are unknowingly turning to such platforms. turned away from the bank for not meeting the income requirements.
The exploitative nature of personal loan terms also many incident of suicide in the Countryto the Government of India start work It is on the allow list of legal digital lending apps allowed by the app store.
Google in August disclosed The company has removed more than 2,000 credit payment apps from the Indian Play Store since the beginning of the year for violating its terms.
the government also wants Urgent Strict Action By law enforcement against loan apps, many of they under Chinese controlhas been found to use harassment, intimidation, and harsh recovery techniques.



