Cybersecurity researchers have discovered weaknesses in software implementations of the Border Gateway Protocol (BGP) that can be weaponized to achieve a denial of service (DoS) condition on vulnerable BGP peers.
Three vulnerabilities exist in version 8.4. FRRoutingis a popular open source Internet routing protocol suite for Linux and Unix platforms.It is currently used by several vendors such as NVIDIA Cumulus, dentand sonicposes supply chain risks.
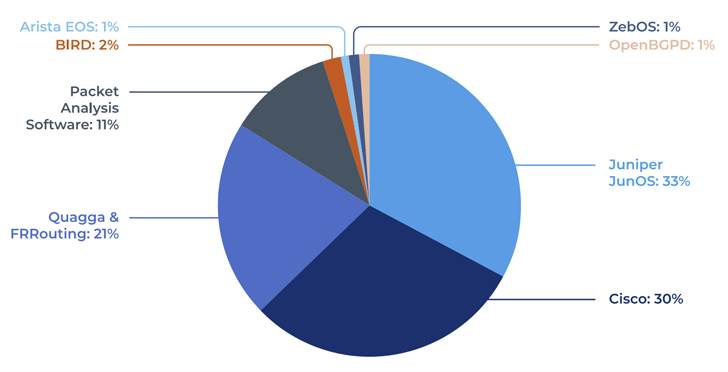
This finding is the result of an analysis of seven different implementations of BGP (FRRouting, BIRD, OpenBGPd, Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS) conducted by Forescout Vedere Labs.
BGP is gateway protocol It is designed to exchange routing and reachability information between autonomous systems. It is used to find the most efficient route for delivering internet traffic.
Here is a list of the three flaws:
- CVE-2022-40302 (CVSS score: 6.5) – Out-of-bounds read when handling malformed BGP OPEN message Use the Extended Optional Parameters Length option.
- CVE-2022-40318 (CVSS Score: 6.5) – Processing a malformed BGP OPEN message with the Extended Optional Parameters Length option causes an out-of-bounds read.
- CVE-2022-43681 (CVSS score: 6.5) – Out-of-bounds read when processing a malformed BGP OPEN message that abruptly ends in an optional length octet.
“This issue could be exploited by an attacker to achieve a DoS condition on a vulnerable BGP peer, resulting in the dropping of all BGP sessions and routing tables, and the peer becoming unresponsive.” Yes,” the company said. report Share with Hacker News.
“Repeatedly sending malformed packets can extend a DoS condition indefinitely. It’s that it’s been copied to some function.”
Threat actors can spoof valid IP addresses of trusted BGP peers, exploit other flaws or misconfigurations to compromise legitimate peers, or issue specially crafted and unsolicited BGP OPEN messages There is a possibility.
This is achieved by taking advantage of the fact that FRRouting begins processing the OPEN message (e.g., decapsulating optional parameters) before it has had a chance to check the originating router’s BGP identifier and ASN fields. will be
Learn how to stop ransomware with real-time protection
Join our webinar to learn how real-time MFA and service account protection can stop ransomware attacks.
Forescout has also made Python-based open source available. BGP fuzzer tool This allows organizations to test the security of their internally used BGP suites and find new flaws in their BGP implementations.
“Modern BGP implementations still have easy outcomes that can be exploited by attackers,” Forescout said. “To reduce the risk of a weak BGP implementation, […] The best recommendation is to patch your network infrastructure devices as often as possible. ”
The findings of this study indicate that ESET router It was previously used in business networking environments and contained sensitive data such as corporate credentials, VPN details, encryption keys, and other important customer information.
“The misuse of data collected from devices, including customer data, router-to-router authentication keys, application lists, etc., is enough to launch a cyberattack,” said the Slovak cybersecurity firm. Said.



