A sophisticated new malware toolkit was discovered after analyzing over 70 billion DNS records. decoy dog It targets enterprise networks.
decoy dogis as evasive as its name suggests, employing techniques such as strategic domain aging and DNS query dribbling, where a series of queries are sent to command and control (C2) domains to arouse suspicion. does not occur.
“Decoy Dog is a cohesive toolkit with a number of highly unusual features that enable unique identification, especially when probing domains at the DNS level,” said Infoblox. Said In an advisory published late last month.
A cybersecurity firm that identified the malware in early April 2023 following unusual DNS beacon activity said its atypical characteristics allowed it to map additional domains that are part of its attack infrastructure.
That said, Decoy Dog is “very rare” to be used in the wild, with DNS signatures matching less than 0.0000027% of the 370 million active domains on the Internet, says the California-based company. says the company that puts
One of the key components of the toolkit is the Pupy RAT. This is an open source Trojan horse that DNS tunnelingDNS queries and responses are used as a C2 to covertly drop payloads.
It is worth noting that the use of the cross-platform Pupy RAT has been associated in the past with Chinese state-state actors such as Earth Berberoka (aka GamblingPuppet), but the fact that the attackers were involved in this campaign There is no evidence to suggest
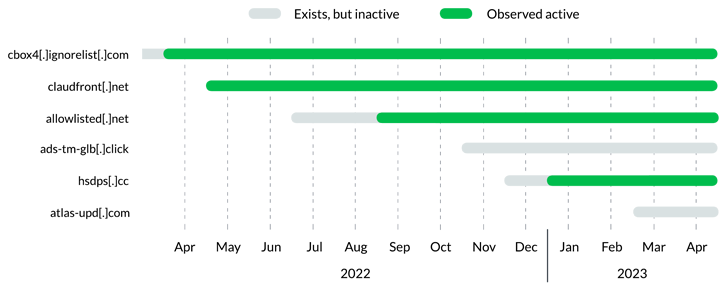
Further investigation of Decoy Dog suggests that the operation began at least a year before its discovery, and that three different infrastructure configurations have been detected to date.
Learn how to stop ransomware with real-time protection
Join our webinar to learn how real-time MFA and service account protection can stop ransomware attacks.
Another important aspect is the unusual DNS beacon behavior associated with the Decoy Dog domain. These domains follow a pattern of regular but infrequent DNS requests that keep them under the radar.
“decoy dog domain We can group based on shared registrars, name servers, IPs, and dynamic DNS providers,” Infoblox said.
“Given other commonalities between Decoy Dog domains, this suggests either a single threat actor evolving tactics over time or multiple threat actors deploying the same toolkit across different infrastructures. shows.”



