The VMware ESXi hypervisor is the target of a new attack designed to deploy ransomware on compromised systems.
France’s Computer Emergency Response Team (CERT) says, “These attack campaigns appear to be exploiting CVE-2021-21974, for which patches have been available since February 23, 2021.” . Said on Friday’s recommendation.
In its own alert released at the time, VMware described the issue as follows: Open SLP A heap overflow vulnerability that could lead to the execution of arbitrary code.
“A malicious actor residing in the same network segment as ESXi with access to port 427 could cause a heap overflow issue in the OpenSLP service, potentially resulting in remote code execution,” said the virtualization service provider. says. I got it.
French cloud service provider OVHcloud Said Attacks have been detected all over the world, especially in Europe. The intrusion is suspected to be related to a new Rust-based ransomware strain called Nevada, which emerged in December 2022.
Other ransomware families known to have adopted Rust in recent months include BlackCat, Hive, Luna, Nokoyawa, RansomExx, and Agenda.
“The attackers are asking both Russian- and English-speaking affiliates to work with a number of Initial Access Brokers (IABs). [the] The Dark Web, “Resecurity” Said last month.
“In particular, the group behind the Nevada Ransomware purchased the compromised access for themselves, and this group has a dedicated post-exploitation team to perform network intrusions on targeted targets. ”
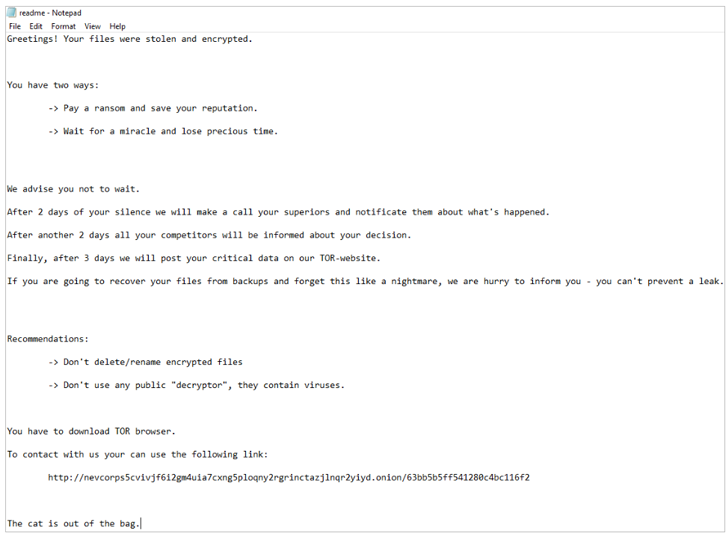
However, Bleeping Computer ransom note It added that what it saw in the attack bears no resemblance to the Nevada ransomware, and that the strain is tracked under the name ESXiArgs.
We recommend upgrading to the latest version of ESXi to mitigate potential threats and restrict access to OpenSLP services to trusted IP addresses.


