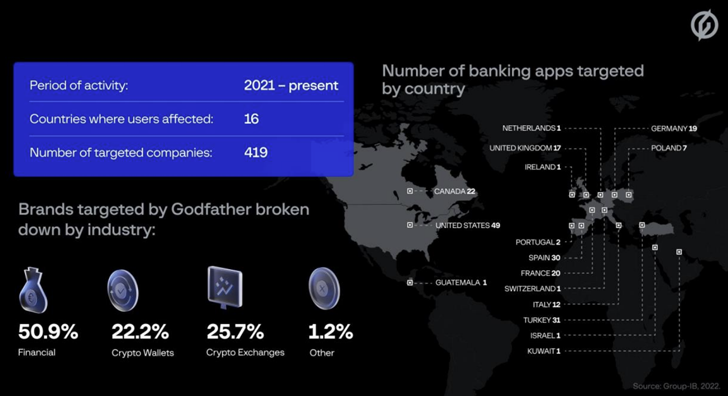
Android banking Trojan known as godfather is used to target users of over 400 banking and cryptocurrency apps across 16 countries.
This includes 215 banks, 94 crypto wallet providers, and 110 crypto exchange platforms serving users in the United States, Turkey, Spain, Italy, Canada, and Canada. Said In a report shared with The Hacker News.
This malware, like many financial Trojans targeting the Android ecosystem, steals user credentials by generating a compelling overlay screen (a.k.a. webfake) that appears on top of the target application. trying to steal
First detected by Group IB in June 2021, Open to the public Created by ThreatFabric in March 2022, GodFather contains a native backdoor that can exploit Android’s accessibility APIs to record videos, log keystrokes, capture screenshots, and collect SMS and call logs. It also has built-in functionality.
Analysis of the malware by Group-IB reveals it to be the successor to the malware. Anubisis another banking Trojan whose source code was leaked on an underground forum in January 2019. It is also said to be distributed to other attackers via a malware-as-a-service (MaaS) model.
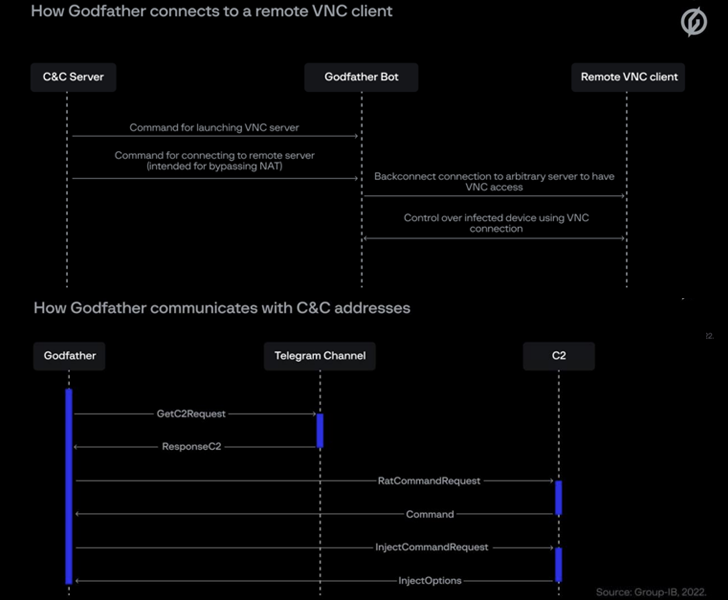
The similarities between the two malware families extend to how they receive command and control (C2) addresses, C2 command implementations, web fakes, proxies, and screen capture modules. However, voice recording and location tracking features have been removed.
“Interestingly, Godfather spares users in post-Soviet countries,” said Group-IB. “If a potential victim’s system settings include any of the local languages, the Trojan will shut down. This suggests that GodFather’s developer is a Russian speaker. may have.”
What makes GodFather stand out is the fact that it obtains command and control (C2) server addresses by encrypting and decrypting descriptions of Telegram channels controlled by the attackers. blowfish code.
Although the exact technique employed to infect user devices is unknown, examination of the threat actor’s command and control (C2) infrastructure suggests that trojanized dropper apps are a potential distribution vector. revealed as one.
This is based on a C2 address linked to an app named Currency Converter Plus (com.plus.currencyconverter) hosted on the Google Play store as of June 2022. The application in question is no longer available for download.
Another artifact investigated by Group-IB masquerades as legitimate Google Play Protect Services to create at startup continuous notification Hides its icon from the list of installed applications.
Findings come as Cyble discovered Numerous GodFather samples masquerading as the MYT Müzik app targeting users in Turkey.
GodFather is not the only Android malware based on Anubis. Earlier this July, ThreatFabric revealed what was known as a modified version of Anubis. falcon Targeted Russian users by impersonating the state-owned VTB bank.
Group-IB researcher Artem Grischenko said:
“With tools like GodFather, threat actors are only limited by their ability to create compelling web spoofs for specific applications. Sometimes the sequel is better than the original. “



