The threat actors behind the Hive Ransomware as a Service (RaaS) scheme have launched attacks against over 1,300 businesses worldwide, making $100 million in fraudulent payments to gangs as of November 2022. brought
“Hive ransomware targets a wide range of businesses and critical infrastructure sectors, including government facilities, telecommunications, critical manufacturing, information technology, especially healthcare and public health (HPH),” US Cybersecurity and Intelligence institution Said in alert.
Active since June 2021, Hive’s RaaS operations include developers who create and manage malware and often purchase initial access from Initial Access Brokers (IABs) to carry out attacks on target networks. There is a mixture of affiliated companies that are responsible for
In most cases, they gain a foothold by exploiting the Microsoft Exchange Server ProxyShell vulnerability, followed by steps to terminate processes related to antivirus engines and data backups, and to delete Windows event logs.
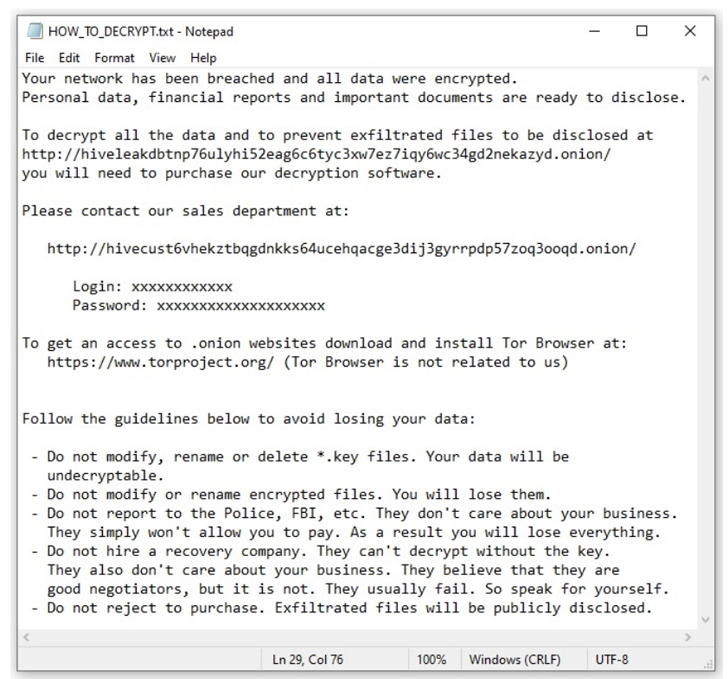
Threat actors who recently upgraded their malware to Rust as an evasion evasion method have also been known to remove virus definitions before encryption.
“Hive attackers are known to use Hive ransomware or another ransomware variant to re-infect the networks of victim organizations that have restored their networks without paying a ransom,” said US Cyber Security and Infrastructure Security Agency (CISA) says:
According to data shared by cybersecurity firm Malwarebytes, Hive compromised about seven victims in August 2022, 14 in September, and two other victims in October, making the group 26 victims. This indicates a decrease in activity since July, when it targeted victims of


