A critical security vulnerability has been identified in the Open Authorization (OAuth) implementation of the application development framework Expo.io.
The downside is that it is assigned a CVE identifier CVE-2023-28131, with a severity rating of 9.6 in the CVSS scoring system. API security company Salt Labs Said This issue made services using this framework susceptible to compromised credentials, which could be used to hijack accounts or exfiltrate sensitive data.
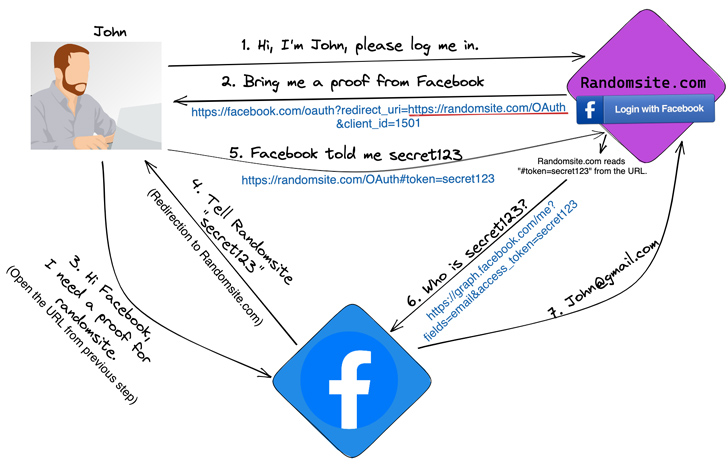
Under certain circumstances, threat actors could use this flaw to perform arbitrary actions on behalf of compromised users on various platforms such as Facebook, Google, and Twitter.
Expo, like Electron, is an open source platform for developing universal native apps that run on Android, iOS and the web.
Note that sites and applications using Expo must configure AuthSession proxy settings for single sign-on (SSO) with third-party providers such as Google and Facebook for the attack to be successful. .
In other words, this vulnerability could be used to send a secret token associated with a sign-in provider (such as Facebook) to an attacker-controlled domain and use it to gain control of the victim’s account. there is.
This is accomplished by tricking targeted users into clicking specially crafted links that may be sent via traditional social engineering vectors such as emails, SMS messages, or questionable websites. increase.
In its advisory, Expo said it deployed the hotfix within hours of its responsible disclosure on February 18, 2023. Transition From using AuthSession API proxies to directly registering deep link URL schemes with third-party authentication providers to enable SSO functionality.
“This vulnerability could allow a potential attacker to trick users into visiting a malicious link, logging into a third-party authentication provider, and accidentally exposing their third-party authentication credentials.” said Expo’s James Ide. Said.
“This is because auth.expo.io is the app’s callback URL Before explicitly confirming that the user trusts the callback URL. ”
Zero Trust + Deception: Learn How to Outsmart Attackers!
See how Deception can detect advanced threats, stop lateral movement, and strengthen your Zero Trust strategy. Join us for an insightful webinar!
The disclosure is as follows discover Booking.com (and its sister site Kayak.com) have similar OAuth issues, allowing them to control users’ accounts, gain full visibility into personal and payment card data, and take action on behalf of victims. It may have been abused for
The findings were also published weeks after Swiss cybersecurity firm Sonar. be familiar with Path traversal and SQL injection flaws in Pimcore enterprise content management system (CVE-2023-28438), an attacker could exploit this to execute arbitrary PHP code on the server with the privileges of the web server.
Sonar also dates back to March 2023 clearly An unauthenticated stored cross-site scripting vulnerability affecting LibreNMS versions 22.10.0 and earlier. Simple Network Management Protocol (SNMP) is enabled.


