what’s happened?
A few days before Christmas, the password management service most people probably didn’t pay much attention to LastPass clearly A hacker has access to the customer’s password vault.
That’s really bad. But wasn’t there news that LastPass was hacked earlier this year?
You’re probably thinking of LastPass’ first announcement on August 25, 2022. It said hackers had successfully accessed a developer’s account and stole some of the source code from the development environment.
LastPass said at the time, “We saw no evidence that this incident involved access to customer data or encrypted password vaults.”
Were they wrong when they said so?
Well, LastPass might not have been saw There is no evidence that the customer’s password vault was accessed at that time…
But when a company says they “didn’t see any evidence” that something bad happened, isn’t that necessarily the same as saying “nothing bad happened”?
correct. Just before Christmas, LastPass revealed that information stolen from a developer’s account in the August 2022 attack was in fact “used to target another employee and gain access to some storage volumes. was used to obtain the credentials and keys used to decrypt with …”.
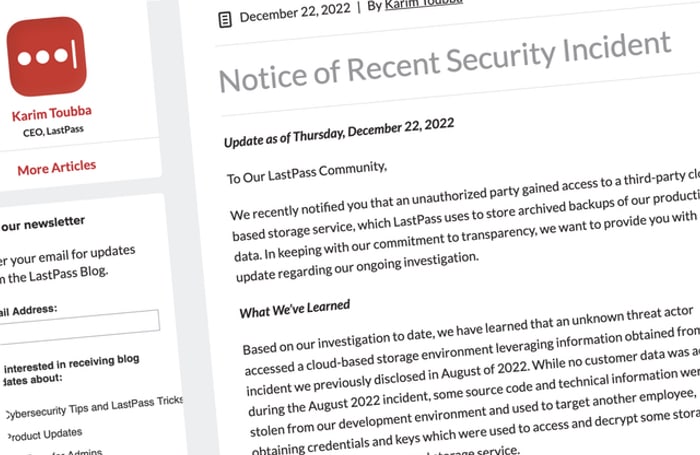
Goku goku! It sounds much worse. To be clear, the theft of password vaults and other data from LastPass may have happened in August or September. It may have happened long before they announced because I was preoccupied with wrapping Christmas presents.
Perhaps. LastPass has not disclosed when it believes the password vault was stolen, but perhaps most importantly, what What the stolen data contained and how it could be misused by hackers.
OK. I am getting dressed. tell me the worst…
Stolen data includes: not encrypted data:
- company name
- end user name
- Billing Address
- telephone number
- email address
- The IP address you used to access LastPass
- Password vault website URL
This means cybercriminals know you use LastPass, how you contact them, and what websites you use.
This is valuable information for anyone trying to phish you for more information, as they may send fraudulent emails spoofing one of the websites you visit.
Plus, just knowing which websites you visit (and store in your password manager) can reveal personal information you might want to keep private.
Additionally, you may have password reset links for these websites stored in your password manager, but they may not have expired. Also, you may not want to store other sensitive information or tokens in your website’s URL and pass them on to malicious users.
This sound is terrible…
Hold on, we’re not done yet.
Hacker stole it too Encrypted Customer data, including:
- Website username and password
- secure notes
- form input data
But it’s encrypted, right?
Yes, it’s encrypted. A hacker must identify LastPass’ master his password in order to access the crown jewels (usernames and passwords for all online accounts).
I have a unique password that is strong and hard to guess. I also have two-factor authentication (2FA) enabled on my LastPass account. So don’t worry…
Hmmm… 2FA is irrelevant in this case. The hacker has already stolen the data in the password vault and doesn’t need to bother logging into someone’s LastPass account.
Likewise, changing your password does not undo the data breach. Of course, it may still be a smart step.
To help hackers, many LastPass users are likely choosing a much weaker master password than LastPass itself recommends.
Since 2018, LastPass says: Recommended It also required a “master password minimum of 12 characters”.
Aside from the fact that character count alone isn’t a good indicator of password strength, customers who have been using LastPass since before 2018 don’t appear to need to update their Master Password to meet LastPass’ own recommendations. Some password vaults are far more vulnerable.
LastPass seems to have missed an opportunity to increase user security…
Yes, rather.
Additionally, security researchers have revealed that at least some of the master passwords that LastPass stores for long-term user vaults are encrypted in a way that’s all too easy to crack.
what do you mean?
As Researcher Vladimir Palant detailLastPass salt-and-hashes the master password using the PBKDF2 algorithm in 100,100 iterations.
The number of “repeats” indicates how much “work” someone (or most likely a modern graphics card) must do to crack the password.
However, many LastPass users who have had accounts for a long time seem to only configure their accounts for 5000 iterations, sometimes 500, or even just one!
Poorly secured vaults like this may not take long (or cost too much) to unlock.

And 1Password as a LastPass competitor I will explainthe numbers are even worse if what hackers are trying to crack is not a truly randomly generated password, but a human-created password.
Oh, by the way, OWASP in 2021 guidance is… error… over 310,000 iterations…
Shouldn’t LastPass, years ago, have reached out to low-iteration customers and forced them to tighten up their security?
I think that was a good idea, right? Years have passed, modern graphics cards have gotten faster at cracking passwords, and LastPass hasn’t been able to better protect its most loyal customers.
The LastPass.com homepage also makes no mention of a data breach. This also seems like a missed opportunity – even closing the stable door after the horse escapes…
Bloomy. Let’s get down to business. Is the LastPass password vault compromised?
Perhaps.
The LastPass Password Vault is more compromised if hackers are ready to invest resources into cracking your master password. For example, if you…
- One of 100,000 businesses worldwide using LastPass
- journalist
- civil servant or politician
- human rights defender
- celebrity
- cryptocurrency investor
- “Persons of interest” to the dictatorship
I am not one of them. I’m just Joe Schmoe. Can I still access passwords saved in the LastPass Vault?
Perhaps. Especially if your password isn’t as strong as it needs to be, or if you’ve reused your Master Password elsewhere on the internet, or if you’ve been exposed to phishing scams, or if LastPass has used your password enough times to Especially if you haven’t strengthened it. to break.
So what should i do?
It is wise to assume that the password has been compromised or could be compromised.
In that case, you need to change your password. *All* passwords stored in your LastPass Vault, not just your LastPass Master Password.
little by little.It’s going to be a lot of work
i hear you I have over 1600 unique passwords in my password vault (I don’t use LastPass, thankfully) and would like to protect other documents as well.
Should You Ditch LastPass?
That’s something only you can decide.
Sorry, LastPass is a product I have recommended to users in the past (they sponsored this website in 2020, and from 2018 to 2020 “Smashing Security” Podcast co-sponsored).
I’ve always been a big fan of password managers (1 password I am also a sponsor of this blog and podcast, Bit Warden It is now a sponsor of “Smashing Security”).
I continue to believe that using a password manager – Almost any password manager – Better than no password manager.
But I can’t bring myself to recommend LastPass right now. There are better options out there.
Where can I find more information?
there are several good blog post On the topic by Vladimir Palant.Also check mastodon thread By Jeremy M. Gosny.
Did you find this article interesting? Follow Graham Cluley on Twitter Also Mastodon To read more about the exclusive content we post.


